This is a simple walkthrough for completing the Crocodile target machine in Hackthebox.com.
Task 1
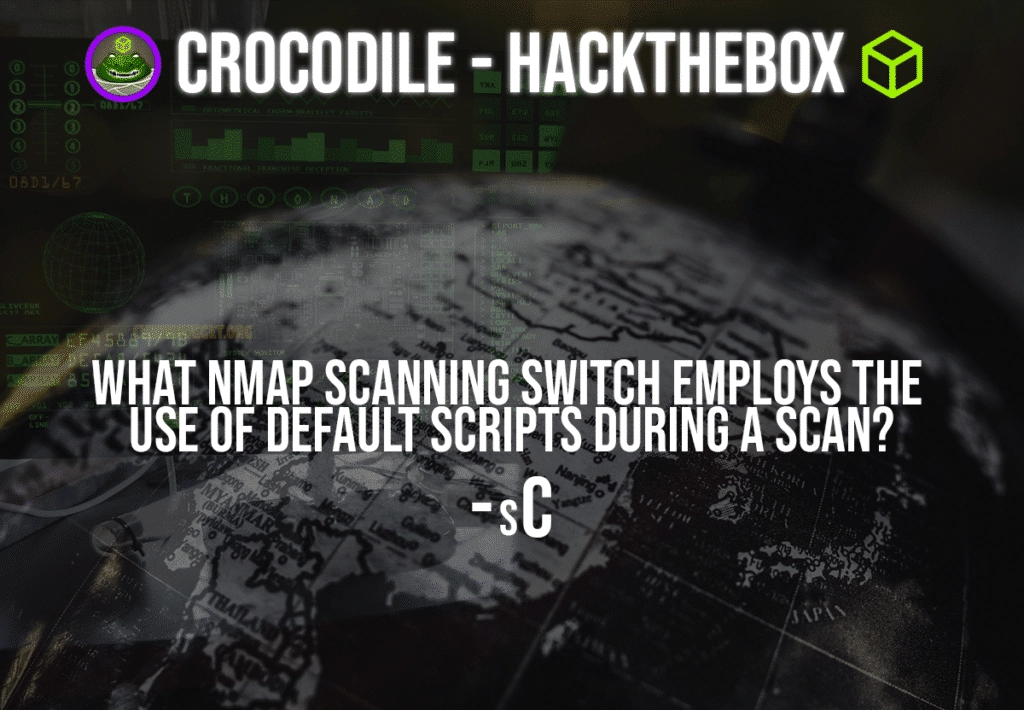
Question: What nmap scanning switch employs the use of default scripts during a scan?
Answer: -sC
Task 2
Question: What service version is found to be running on port 21?
Answer: vsftpd 3.0.3

Task 3
Question: What FTP code is returned to us for the “Anonymous FTP login allowed” message?
Answer: 230

Task 4
Question: What command can we use to download the files we find on the FTP server?
Answer: get

Task 5
Question: What is one of the higher-privilege sounding usernames in the list we retrieved?
Answer: admin

Task 6
Question: What version of Apache HTTP Server is running on the target host?
Answer:

Task 7
Question: What is the name of a handy web site analysis plug-in we can install in our browser?
Answer: wappalyzer

Task 8
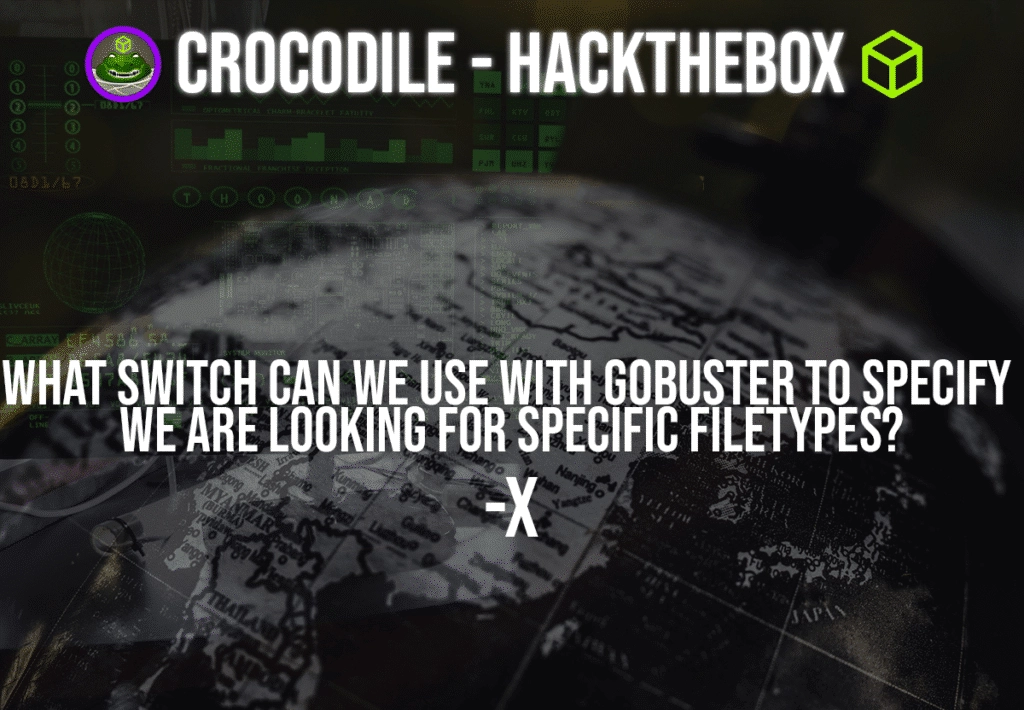
Question: What switch can we use with gobuster to specify we are looking for specific filetypes?
Answer: -x
Task 9
Question: What file have we found that can provide us a foothold on the target?
Answer: login.php
We were able to enumerate these files by using the following command:
$ gobuster dir -u 10.129.106.51 -w /usr/share/dirb/wordlists/common.txt -x php
Task 10
Submit flag
From the previous step, we can see that there is a login.php webpage. If we navigate to this webpage we can see there is an actual login form to enter credentials. If we go back a couple steps, we can remember that there was FTP functionality in this box, which means we can take a look to see if there are any stored usernames or passwords.
We know that this box is misconfigured and has anonymous login allowed for FTP. If we login with the FTP username as anonymous, there we can see two files available.

From here, we can use the get command in FTP to download those files so we can view the contents.
get allowed.userlistget allowed.userlist.passwd
There are only a couple of usernames and passwords in this list. We will just enter them manually into the login prompt. If there was a larger list to use for brute forcing, we could use an automated tool for that. In this case, the admin username worked with one of the passwords and we were successfully able to login.
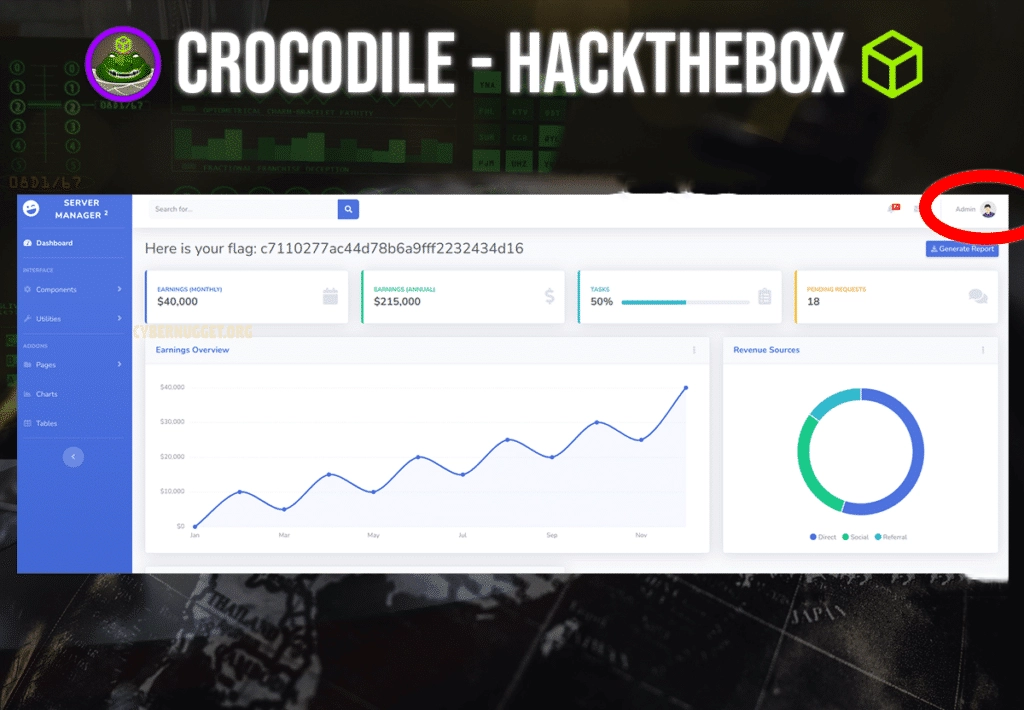
Mission accomplished.
FTP Commands
FTP Command Description of Command
! Escape to the shell.
$ Execute macro
? Print local help information.
account Send account command to remote server.
append Append to a file.
ascii Set ascii transfer type.
beep Beep when command completed.
binary Set binary transfer type.
bye Terminate FTP session and exit.
case Toggle mget upper/lower case id mapping.
cd Change remote working directory.
cdup Change remote working directory to parent directory.
chmod Change file permissions of remote file.
close Terminate FTP session.
cr Toggle carriage return stripping on ascii gets.
debug Toggle/set debugging mode.
delete Delete remote file
dir List contents of remote directory.
disconnect Terminate FTP session.
exit Terminate FTP sessions and exit.
form Set file transfer format.
get Receive file.
glob Toggle meta character expansion of local file names.
hash Toggle printing ‘#’ for each buffer transferred.
help Display local help information.
idle Get (set) idle timer on remote side.
image Set binary transfer type.
ipany Allow use of any address family.
ipv4 Restrict address usage to IPv4.
ipv6 Restrict address usage to IPv6.
lcd Change local working directory.
ls List contents of remote directory.
macdef Define a macro.
mdelete Delete multiple files.
mdir List contents of multiple remote directories.
mget Get multiple files.
mkdir Make directory on remote machine.
mls List contents of multiple remote directories.
mode Set file transfer mode.
modtime Show last modification time of remote file.
mput Send multiple files.
newer Get file if remote file is newer than local file.
nlist List remote directory nlist contents.
nmap Set templates for default file name mapping.
ntrans Set translation table for default file name mapping.
open Connect to remote ftp.
passive Enter passive transfer mode.
prompt Force interactive prompting on multiple commands.
proxy Issue command on an alternate connection.
put Send one file.
pwd Print working directory on remote machine.
qc Print ? in place of control characters on stdout.
quit Terminate ftp session and exit.
quote Send arbitrary ftp command.
recv Receive file.
reget Get file restarting at end of local file.
rename Rename file.
reset Clear queued command replies.
restart Restart file transfer at bytecount.
rhelp Get help from remote server.
rmdir Remove directory on remote machine.
rstatus Show status of remote machine.
runique Toggle store unique for local files.
send Send one file.
sendport Toggle use of PORT cmd for each data connection.
site Send site specific command to remote server.
size Show size of remote file.
status Show current status.
struct Set file transfer structure.
sunique Toggle store unique on remote machine.
system Show remote system type.
tenex Set tenex file transfer type.
tick Toggle printing byte counter during transfers.
trace Toggle packet tracing.
type Set file transfer type.
umask Get (set) umask on remote site.
user Send new user information.
verbose Toggle verbose mode.Gobuster Commands
Usage:
gobuster [command]
Available Commands:
dir Uses directory/file enumeration mode
dns Uses DNS subdomain enumeration mode
fuzz Uses fuzzing mode
help Help about any command
s3 Uses aws bucket enumeration mode
version shows the current version
vhost Uses VHOST enumeration mode
Flags:
--delay duration Time each thread waits between requests (e.g. 1500ms)
-h, --help help for gobuster
--no-error Don't display errors
-z, --no-progress Don't display progress
-o, --output string Output file to write results to (defaults to stdout)
-p, --pattern string File containing replacement patterns
-q, --quiet Don't print the banner and other noise
-t, --threads int Number of concurrent threads (default 10)
-v, --verbose Verbose output (errors)
-w, --wordlist string Path to the wordlist
-x Looks for files specified
Use "gobuster [command] --help" for more information about a command.CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.


