Firewalls and Intrusion Prevention Systems (IDS) have become more advanced over the years with the ability to detect various sophisticated attacks. Although the technology in these systems exists to detect network scanning, who is to say that the system administrator might have forgotten to fix a misconfigured server?
This is why scanning with specific techniques is important if you ever come across a network that keeps dropping your packets or if the network keeps returning all ports are up. With some luck, the following NMAP techniques could allow you to perform NMAP scanning without getting caught by system rules.
- Using Rotating Proxy Service
- Using Proxy Chains
- Sending Fragmented Packets
- Sending Maximum Transmission Unit (MTU) Packets
- Sending Bad Checksums
- Use a Decoy Scan
- Change Data Length
- IP/MAC Spoofing
- Discover Firewall Rules (firewalking)
- Scan Speed
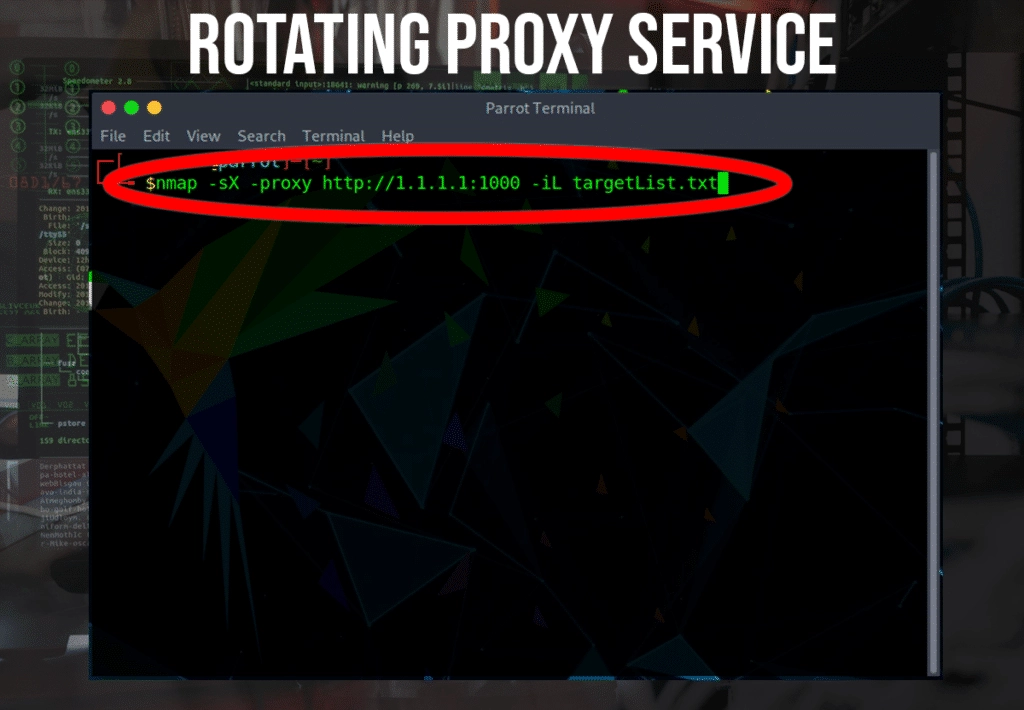
Rotating Proxy Service
Works by connecting to a single IP address out to the internet using any number of rotating proxies
$ nmap -sX -proxy http://1.1.1.1:1000 -iL targetList.txt
Proxy Chains
Rather than using a single proxy, proxychains allows the ability to string together multiple proxies, making it harder to detect the source IP address. Once proxychains is installed on your Linux system, you can edit the proxychains conf file to add a list of proxies that you want to chain together.
Running proxychains is fairly simple, The command is:
$ proxychains <command>
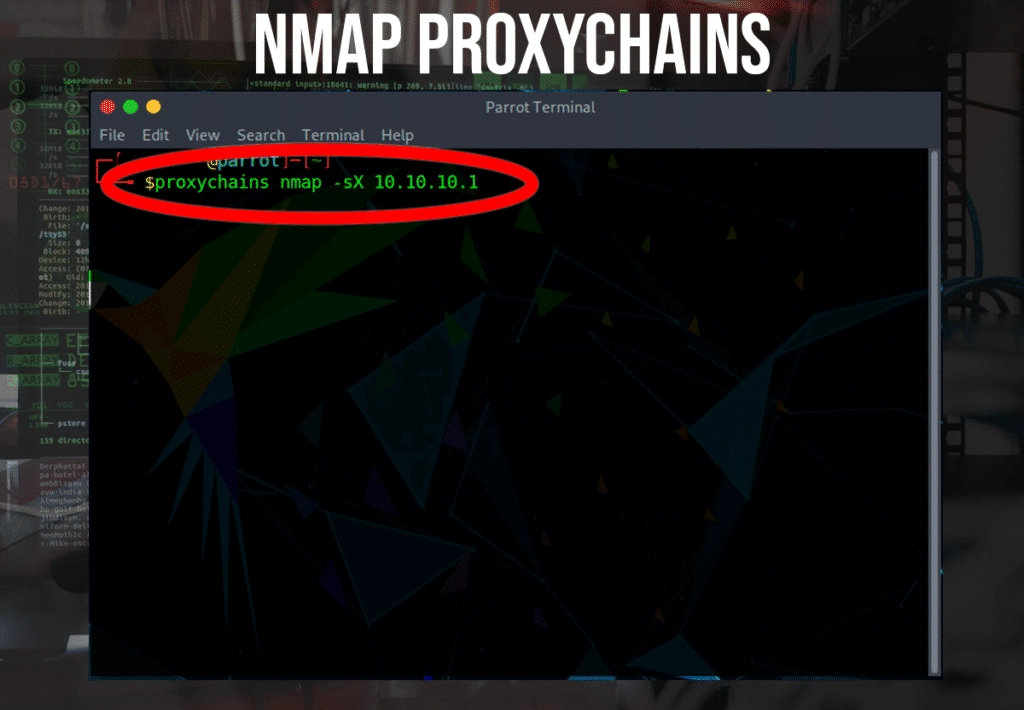
Running an NMAP command through proxychains:
$ proxychains nmap -sX 10.0.0.1
The service StormProxies does this for you without having to worry about setting up your own proxy network.
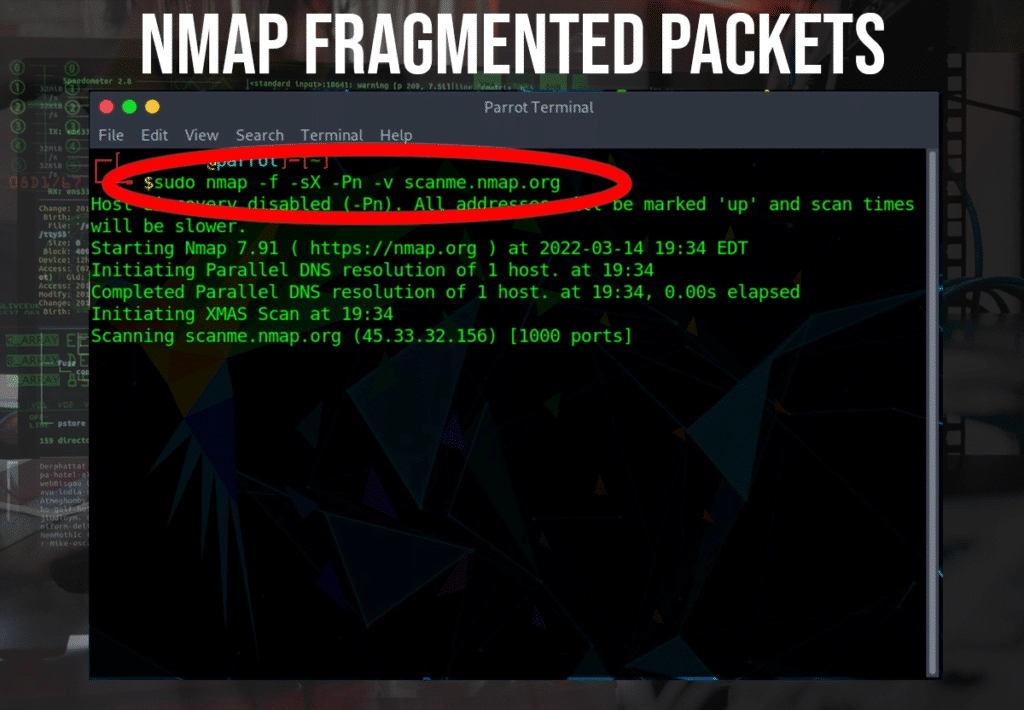
Fragmented Packets
Very unlikely that a fragmented packet will work, it’s worth trying in case there is a misconfigured IDS. The -f flag tells NMAP to send 8-byte packets, fragmenting the probe into much smaller packets:
$ nmap -f -sX -Pn -v scanme.nmap.org
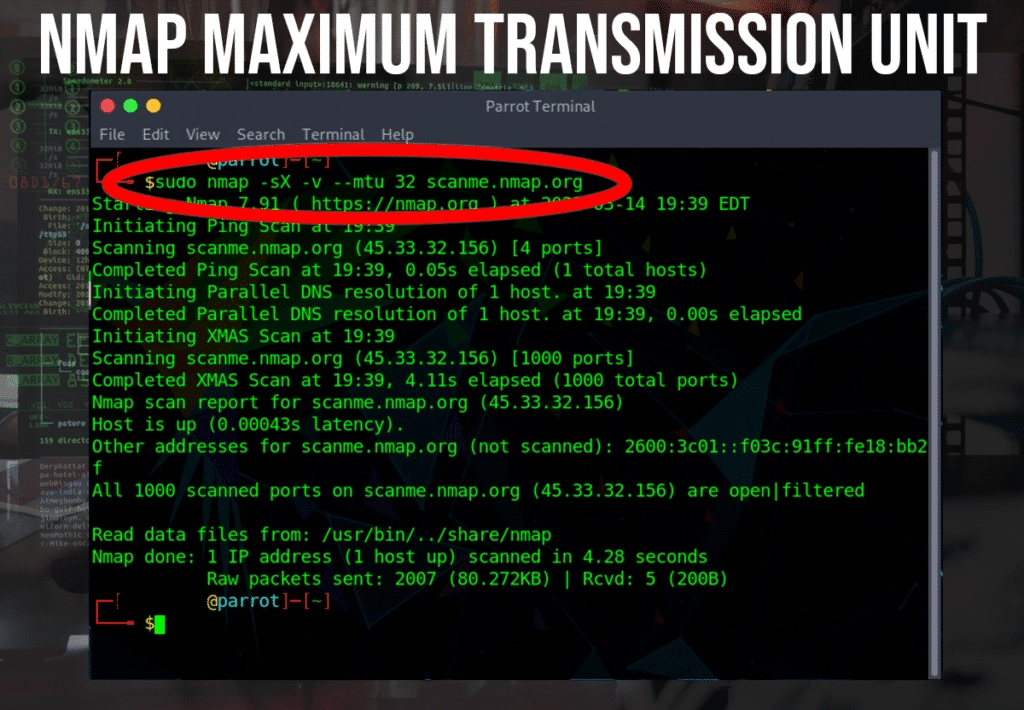
Maximum Transmission Unit (MTU) Packets
The –mtu command is similar to the -f flag in that it sends a limited amount of data during transmission. It could potentially confuse older firewalls.
$nmap -sX -v –mtu 32 scanme.nmap.org
Sending Bad Checksums
The TCP/IP protocol uses checksums to ensure data integrity. By crafting packets with incorrect checksum information, we might be able to trick the target host into sending a response. The -badsum switch is used for this.
$ nmap -sX -T4 –badsum scanme.nmap.org

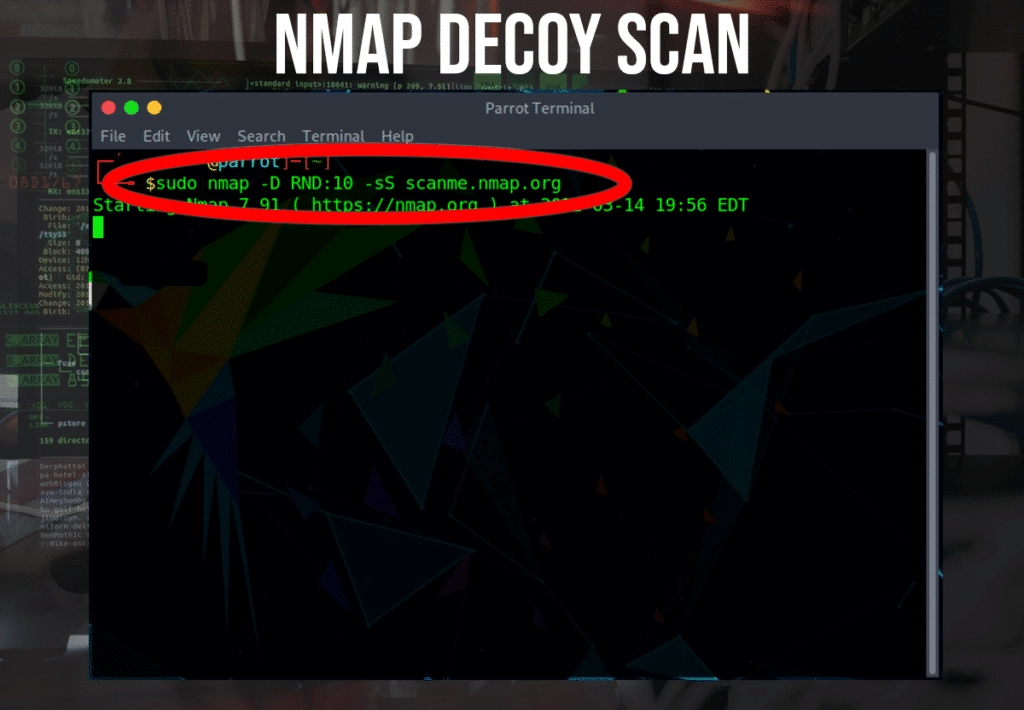
Decoy Scan
When performing a decoy scan, NMAP will spoof additional packets that appear to be coming from a number of different spoofed decoy addresses. This might make a host think that it is being bombarded from multiple systems simultaneously and cause the IDS/firewall to ignore the scans from our main system.
To include decoy scans, use the -D command followed by RND:[number], which will tell NMAP to generate [number] random decoys.
$ nmap -D RND:10 -sS scanme.nmap.org
Change Data Length
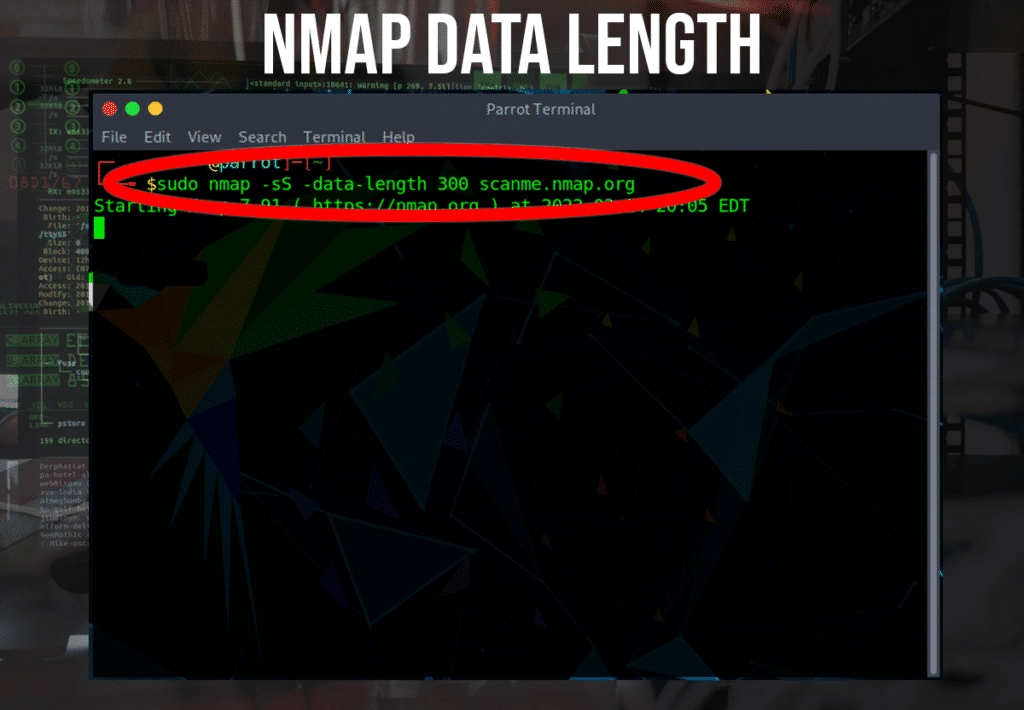
Many port scanners send the same size requests to a target host, so firewalls/IDS are typically designed to detect port scans by looking at the size of the packet. To change the size of the packet and try to avoid firewall detection, use the -data-length argument and specify the data to be sent with the packet.
$ nmap -sS -data-length 300 scanme.nmap.org
IP/MAC Spoofing
You will need to know the MAC address of a device inside the network. If you know what vender the target is using, you can try and gather MAC addresses from that vendors specific products. Spoofing a MAC address is best used when on internal network scans when you know the exact MAC. You can also spoof an IP address so the target thinks you are coming from that host. Spoofing the IP address will mean you will never see the return packet unless you have access to that IP address. Spoofing an IP address also requires you to bind your request to a network interface using the -e switch. This requires you to set up a fake internal network on your computer (like fnic01) and send the requests from there.
MAC EXAMPLE: $ nmap -sF -e fnic01 -spoof-mac <mac address> facebook.com
IP EXAMPLE: $ nmap -sF -e fnic01 -S 192.168.0.150 facebook.com
Firewall Rules (firewalking)
Firewalking gathers information about a host by using an IP TTL (time-to-live) expiration alogirthm to determine if a host is active or not. Essentially, the route to the host is determined by using traceroute. A packet is then sent to the host with a time-to-live value equal to the distance to the target. If the packet times out, it is resent with the previous value minus one. If the host comes back with a time-to-live exceeded (ICMP type 11 code 0), that means the packet was forwarded and the port is not blocked. If no response is received, the port is blocked at the gateway. Since traceroute is dependent on an IP layer (the time-to-live field), any transport protocol can be used the same way (TCP, UDP, ICMP). NMAP has a built in script that can before firewalking. The script will try to discover the firewall rules using the IP TTL expiration method.
$nmap –script=firerwalk –script-args=firewalk.max.probed.ports=5 \ –traceroute host
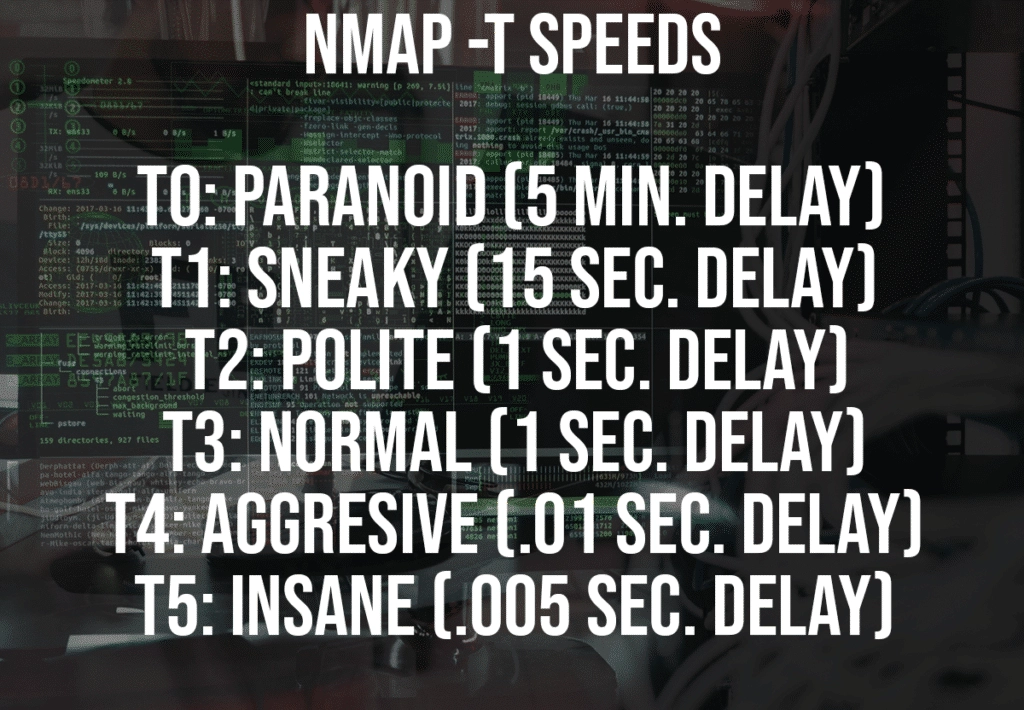
Scan Speed
The NMAP -t switch will change the timing between requests. This potentially could lead to fooling the detection system. While lowering the speed might or might not allow you to avoid detection, it will dramatically increase your scan time. The default NMAP scan is set to -T3. Below is a table describing the speeds.
Timing templates and their effects (values in milliseconds)
| T0 | T1 | T2 | T3 | T4 | T5 | |
| Name | Paranoid | Sneaky | Polite | Normal | Aggressive | Insane |
| min-rtt-timeout | 100 | 100 | 100 | 100 | 100 | 50 |
| max-rtt-timeout | 300,000 | 15,000 | 10,000 | 10,000 | 1,250 | 300 |
| initial-rtt-timeout | 300,000 | 15,000 | 1,000 | 1,000 | 500 | 250 |
| max-retries | 10 | 10 | 10 | 10 | 6 | 2 |
| Initial (and minimum) scan delay (–scan-delay) | 300,000 | 15,000 | 400 | 0 | 0 | 0 |
| Maximum TCP scan delay | 300,000 | 15,000 | 1,000 | 1,000 | 10 | 5 |
| Maximum UDP scan delay | 300,000 | 15,000 | 1,000 | 1,000 | 1,000 | 1,000 |
| host-timeout | 0 | 0 | 0 | 0 | 0 | 900,000 |
| min-parallelism | Dynamic, not affected by timing templates | |||||
| max-parallelism | 1 | 1 | 1 | Dynamic | Dynamic | Dynamic |
| min-hostgroup | Dynamic, not affected by timing templates | |||||
| max-hostgroup | Dynamic, not affected by timing templates | |||||
| min-rate | No minimum rate limit | |||||
| max-rate | No maximum rate limit | |||||
| defeat-rst-ratelimit | Not enabled by default |
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.


