Hypertext Markup Language (HTML) injection is a type of injection vulnerability that occurs when a user is able to control an input point such as a search form and is able to inject arbitrary HTML code.. HTML allows web users to create and structure sections, paragraphs, and links using elements, tags, and attributes. However, it’s worth noting that HTML is not considered a programming language as it can’t create dynamic functionality.
Injecting HTML in a vulnerable web page takes advantage of non-validated input to modify a web page presented by a web application to its users. This is typically caused from poor security programming practices on the developer side. HTML Injection can have many consequences, such as: disclosure of a user’s session cookies that could be used to impersonate the victim, or, more generally, it can allow the attacker to modify the page content seen by the victims.
The below walkthrough will be conducted using the TryHackMe environment lab.

Using on of TryHackMe’s vulnerable web pages provided, we will see that there is a directory search form. In this search form, we can simply try and enter a simple HTML line of code to see if it parses the information.
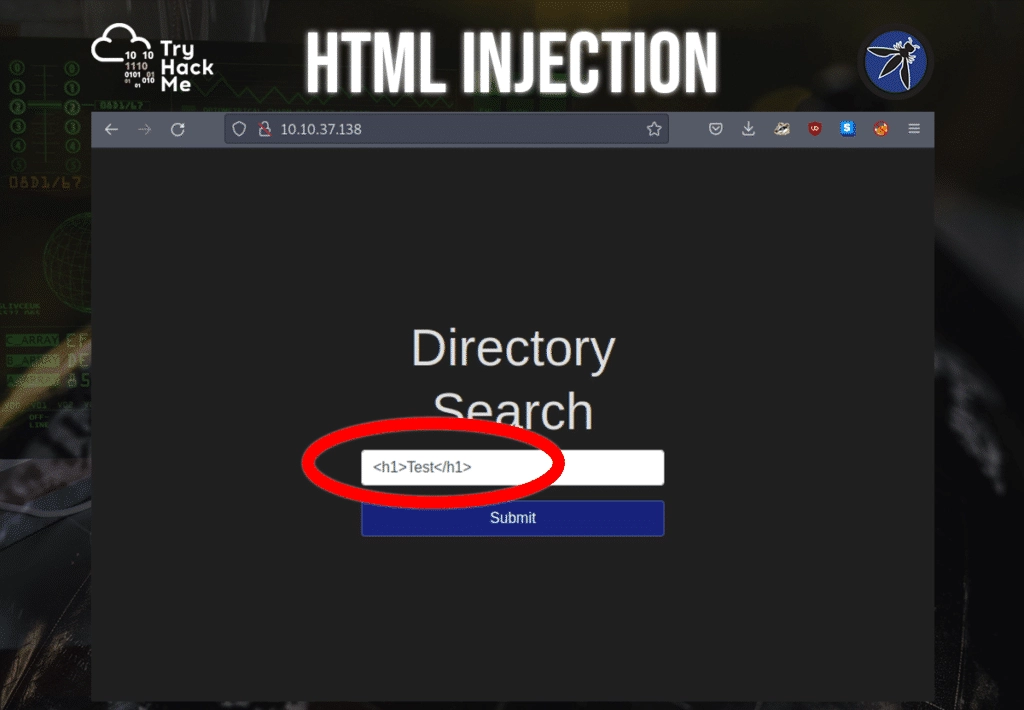
We will be using the h1 tag as a simple input and when submitting, we see the page below.
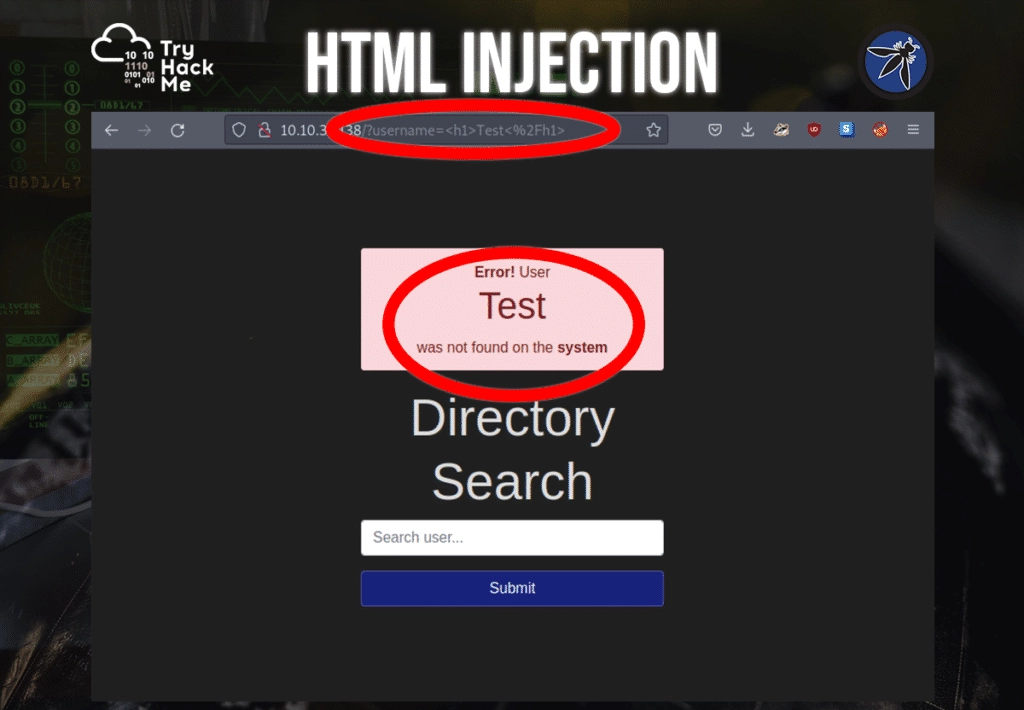
As you can see, this web page does not properly sanitize the user submitting string and prompts the web page with the ‘Test’ string as an H1 tag. You can try this with other common HTML tags.
| HTML Tag | Tag Explained |
|---|---|
| <TITLE> . . . </TITLE> | The title of the document |
| <H1> . . . </H1> | First-level heading large text size |
| <H2> . . . </H2> | Second-level heading |
| <H3> . . . </H3> | Third-level heading |
| <H4> . . . </H4> | Fourth-level heading |
| <H5> . . . </H5> | Fifth-level heading |
| <H6> . . . </H6> | Sixth-level heading small text size |
| <P> . . . (</P>)* | Paragraph Hitting a return in the HTML file will not make a new paragraph when the file is viewed. You need to use this tag to make a new paragraph. |
| <BR> | Line Break This tag will show a blank line. |
To detect HTML injection, look for HTML elements in the incoming HTTP stream that contains the user input. A naïve validation of user input simply removes any HTML-syntax substrings (like tags and links) from any user-supplied text. In other words, sanitize user inputs before processing.
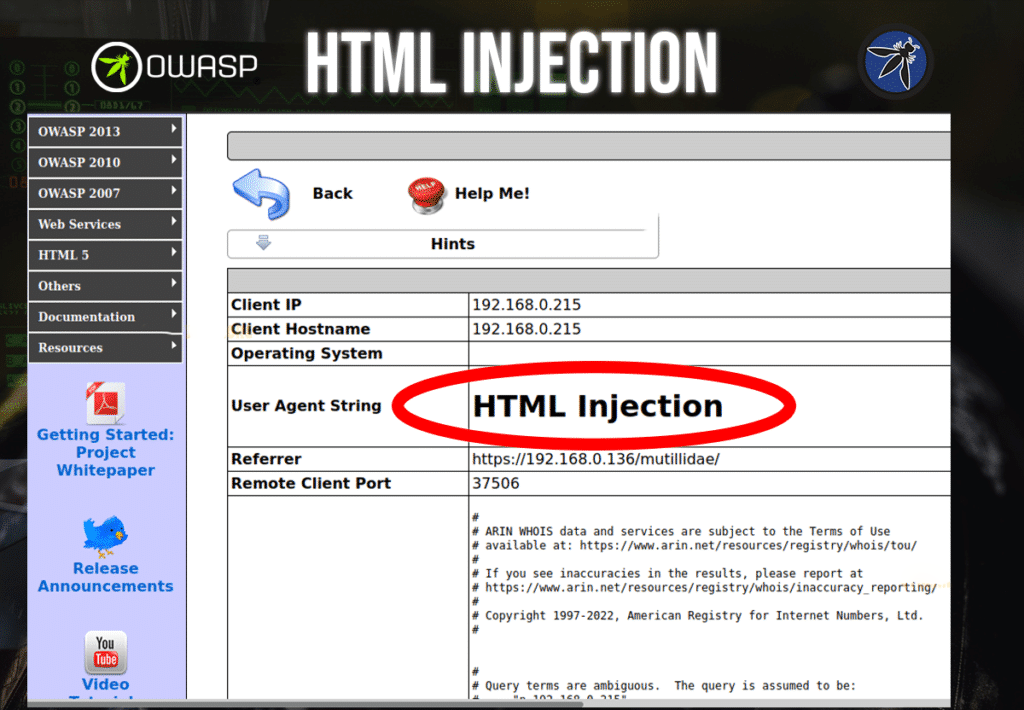
We can also do HTML injection by using Burp Suite and intercepting the packets inside the OWASP Broken Web Application (BWA) Project site. Inside the OWASP BWA, naviagte to A1 – Injection (Other) -> HTML Injection -> Browser Info.
Here we have a web page with simple browser information from our session. There are no input fields here as we saw in the previous example.
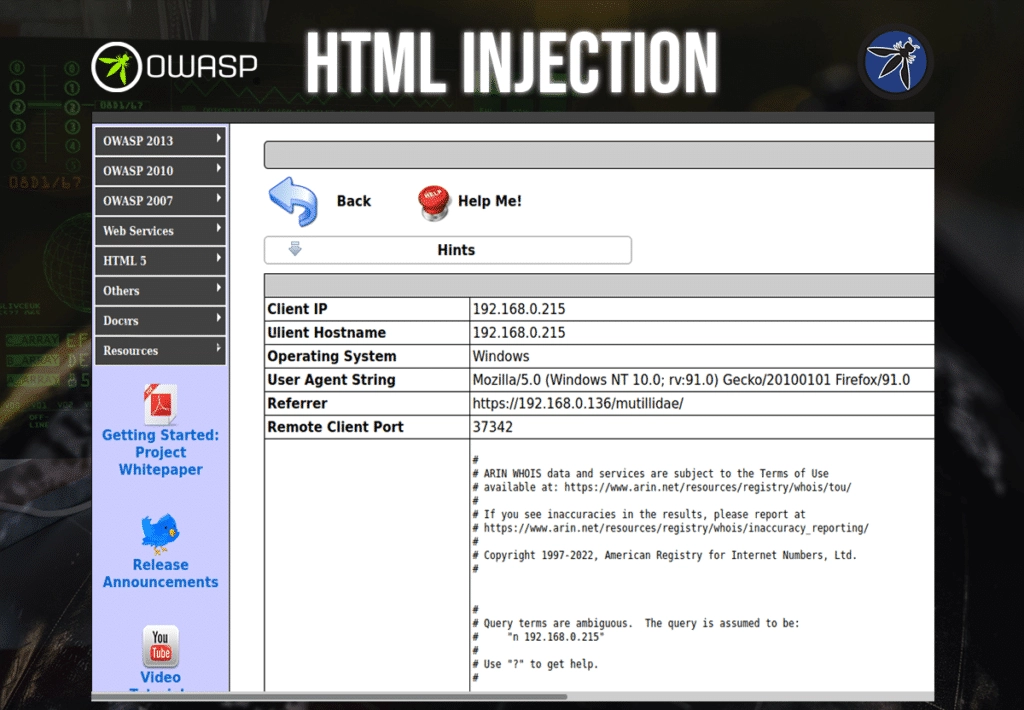
What we can do in this particular situation is try and inject HTML code using Burp Suite. We will focus on the User Agent String.
Fire up Burp Suite and reload the web page to intercept the traffic and make sure the proxy is turned on. You should see the following request inside Burp Suite as shown below:

The user-agent field is where we are going to insert the HTML to see if it reflects on the web page. In here, type HTML code in the field and forward the packet.
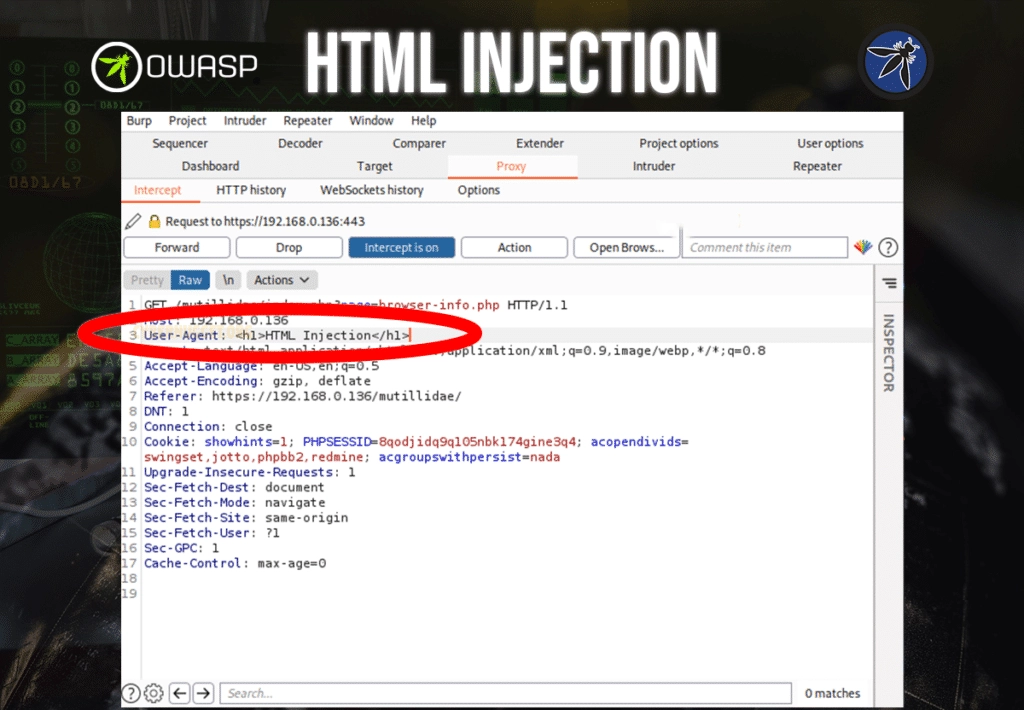
Once this request is forwarded, you will see that the we successfully injected HTML in this web application as shown below.
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.


