What is spoofing?
In the context of Cybersecurity, spoofing is the art and science of pretending to be someone else by compromising the trusted senders communication. There are a number of different ways spoofing can be performed via various forms of communication. Some examples include via Short Message Service (SMS), voice, Internet Protocol (IP), e-mail, Domain Name System (DNS), Media Access Control (MAC) address, and many other types of logical identification.
One of the primary goals of spoofing is to steal someone else’s identity to bypass filters and blockages. After a successful spoofing attack, other forms of attacks can be initiated such as privilege escalation, back-doors, Distributed Denial of Service (DDoS), or data theft – to name a few.
IP Address Spoofing
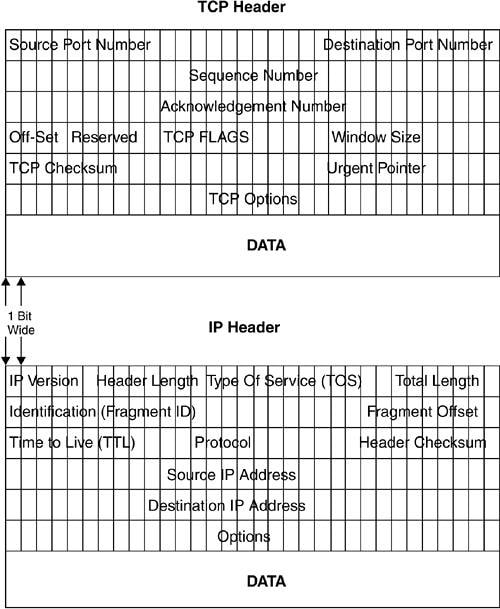
To understand IP address spoofing, you must first understand how a basic TCP/IP handshake works. Throughout communication, many packets are sent and once they reach their destination, they are assembled. Every packet sent contains what is called an IP Header. This IP Header contains basic information such as the source IP address and destination IP address. Take a look at the image below. This is an example of an IPv4 IP Header.

There is a lot going on in that packet but for now, focus in on only the source and destination address highlighted.
In normal IPv4 communication, the packets are sent using the TCP/IP protocol. This TCP/IP protocol suite is what makes spoofing available to hackers. The reason for this is because the TCP/IP protocol requires the source and destination address to complete a three-way handshake using IP addresses. Below you will see the basics of what goes on behind the scenes on your computer when you are browsing the internet using a three-way handshake.
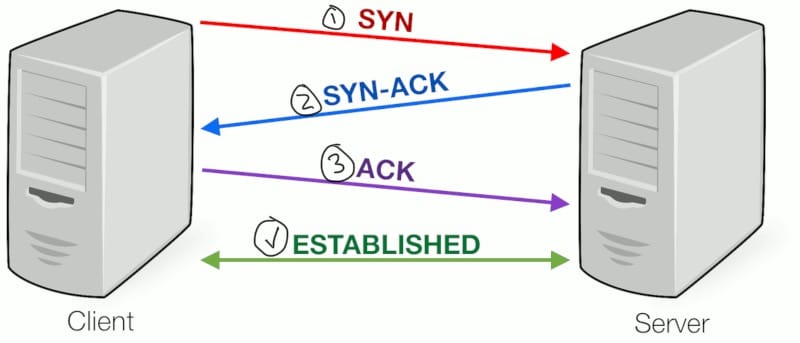
The three terms used in a TCP/IP three-way handshake are SYN, SYN-ACK, and ACK. As you can see above, the client (meaning you) sends a SYN packet saying something along the lines of “hi, is there anybody there?”. The server (website you are visiting) replies back with a SYN-ACK, basically saying “yes I am here.”. Finally, when the client (you) receive that SYN-ACK from the server, you reply back with an ACK and the communication is established.
| SYN | Synchronize | Request synchronize with new sequence numbers. |
| ACK | Acknowledge | Acknowledges synchronization or shutdown request. |
| RST | Reset | Reset will cause an immediate and abrupt session termination. |
| FIN | Finish | Takes 4 FIN packets to gracefully tear down a tcp connection. |
IP Spoofing Example
IP address spoofing takes advantage of the TCP/IP three-way handshake. Note that the IP header and TCP header contain different information, which is how the attacker is able to execute this attack. The attacker managed to get your IP address from the IP header.

Now that the attacker has this information, they are going to try and intercept the three-way handshake process using the TCP header. The TCP header has what is called a Sequence Number as shown below.
This sequence number is the trick behind the IP address spoofing. Before you are able to finalize the established connection by sending the ACK response to the website you are visiting, the attacker will do this first. This allows the attacker to fully establish the connection to the website you were trying to visit. The attacker is able to do this if they can guess or predict the sequence number correctly. After the attacker beats you to send the ACK segment first, the website is now going to trust the attacker because they spoofed your IP address making it look like you who initially sent the SYN “hi, is there anybody there?” packet.
“Segments in a TCP transmission are tagged with a sequence number. This allows the receiver to rebuild the original communication by reordering received segments back into their proper arrangement in spite of the order they were received.”
Guessing Sequence Number in TCP Connection
Guessing or predicting the correct sequence number in a TCP packet depends on the type of spoofing attack being performed. There are two types of attacks, which include nonblind spoofing and blind spoofing.
Nonblind spoofing occurs when you and the attacker are on the same subnet. This allows the attacker to use a packet capture tool such as Wireshark to keep note on the sequence numbers.
Blind spoofing is the most common as same access to victim subnet is not common and it occurs when the attacker uses IP source routing, sequence number prediction, or single packet spoofing.
IP Spoofing Tutorial using Blind Spoofing
Sequence Number Prediction
The blind spoofing form of attack using sequence number prediction allows the attacker to brute force or take educated guesses at the SYN-ACK sequence number. This is a fairly difficult task for a number of reasons. First, to successfully guess the sequence number, the attacker is faced with any random value between 0 and 4,294,967,295.
(Side note* if you are using Wireshark to look at sequence numbers, they display Relative sequence numbers meaning the actual value is not shown. The reason for this in Wireshark is because it is much easier to keep note at relative sequence numbers, meaning much shorter numbers such as 1 or 5 as opposed to a large number in the millions. If you want the actual sequence number to show up you can change the settings or look deeper in that packet and use the ANCII decode.)
Generally speaking, there are a couple ways that servers generate sequence numbers. Knowing the ways a server generates sequence numbers will allow you to make educated predictions as opposed to randomly guessing. These methods include the 64k technique, time incrementation technique, and the modern technique.
64k Technique Concept: This technique is geared more towards older operating systems. They have two sets of rules that allows them to generate sequence numbers.
- The sequence number counter is incremented every second by 128,000.
- The sequence number counter is incremented by 64,000 every time a new connection is established.
64k Technique Attack Methodology: To verify this attack works, the attacker would send a packet (not spoofed) to the server. The attacker proceeds to examine the sequence number, and repeating this process while validating if the sequence numbers added up can be divided by 64,000.
Time Incrementation Technique: Some operating systems use what is called the time incrementation technique, which is relatively easy to crack. This technique tells the server to increment the sequence number x amount of times for every unit of time. This means that the server could change the sequence number up by 1 every 1 second.
Time Incrementation Technique Attack Methodology: To successfully try and figure out the sequence number for operating systems using this technique, an attacker could try and brute-force the sequence number by guessing. Some operating systems using this technique will send back a RST packet when the sequence number guessed is larger than the real one sent.
Modern OS Technique: The most recent Operating Systems use random number generators. This is the most difficult to crack – sometimes even impossible.
IP Source Routing For IP Spoofing
The concept used in IP source routing is that the attacker can specify a route the packet takes, rather than just letting the packet go through routers. The reason this works is because the attacker picks the packets routes and can have a spoofed address, which makes the spoofing attack non-blind. The reason it is non-blind is because unlike trying to randomly predict sequence numbers, the attacker will receive packets back.
SYN Flood Attack
Another reason why brute forcing the sequence number is a difficult task is because the client (you) can reply back to the website with a RST (reset) packet indicating you want to reset the connection because it was not expecting the SYN-ACK packet. In an attacker point of view, a simple way you can prevent the client from sending a RST packet is by performing a SYN flood attack.
Tools used for IP Spoofing
There are many tools online that will help with IP spoofing, especially the more difficult techniques such as sequence number guessing.
- SEQ-Scan www.thenewbiesarea.com/texts/anonym…ipspoofing2.htm
- Mendax – rootshell.com/archive-j457nxiqi3gq5…endax_Linux.tgz
- DSniff – www.monkey.org/%7Edugsong/dsniff/
- Spoofit.h – www.thenewbiesarea.com/texts/anonym…ipspoofing1.htm
All information on this post is for educational purposes only.
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.


