This is a simple walkthrough for completing the Dancing target machine in Hackthebox.com.
Task 1
Question: What is considered to be one of the most essential skills to possess as a Penetration Tester?
Answer: dir busting

Task 2
Question: What switch do we use for nmap’s scan to specify that we want to perform version detection?
Answer: -sV

Task 3
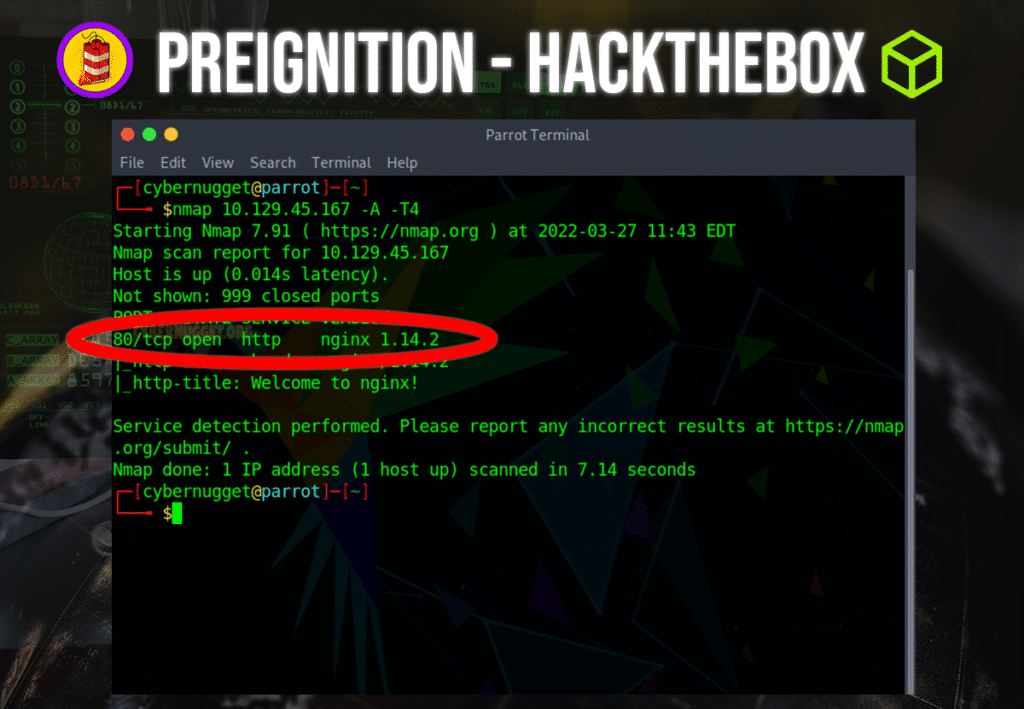
Question: What service type is identified as running on port 80/tcp in our nmap scan?
Answer: http
Task 4
Question: What service name and version of service is running on port 80/tcp in our nmap scan?
Answer: nginx 1.14.2

Task 5
Question: What is a popular directory busting tool we can use to explore hidden web directories and resources?
Answer: Gobuster

Task 6
Question: What switch do we use to specify to gobuster we want to perform dir busting specifically?
Answer: dir

$gobuster -h
Usage:
gobuster [command]
Available Commands:
dir Uses directory/file enumeration mode
dns Uses DNS subdomain enumeration mode
fuzz Uses fuzzing mode
help Help about any command
s3 Uses aws bucket enumeration mode
version shows the current version
vhost Uses VHOST enumeration mode
Flags:
--delay duration Time each thread waits between requests (e.g. 1500ms)
-h, --help help for gobuster
--no-error Don't display errors
-z, --no-progress Don't display progress
-o, --output string Output file to write results to (defaults to stdout)
-p, --pattern string File containing replacement patterns
-q, --quiet Don't print the banner and other noise
-t, --threads int Number of concurrent threads (default 10)
-v, --verbose Verbose output (errors)
-w, --wordlist string Path to the wordlist
Use "gobuster [command] --help" for more information about a command.Task 7
Question: What page is found during our dir busting activities?
Answer: admin.php
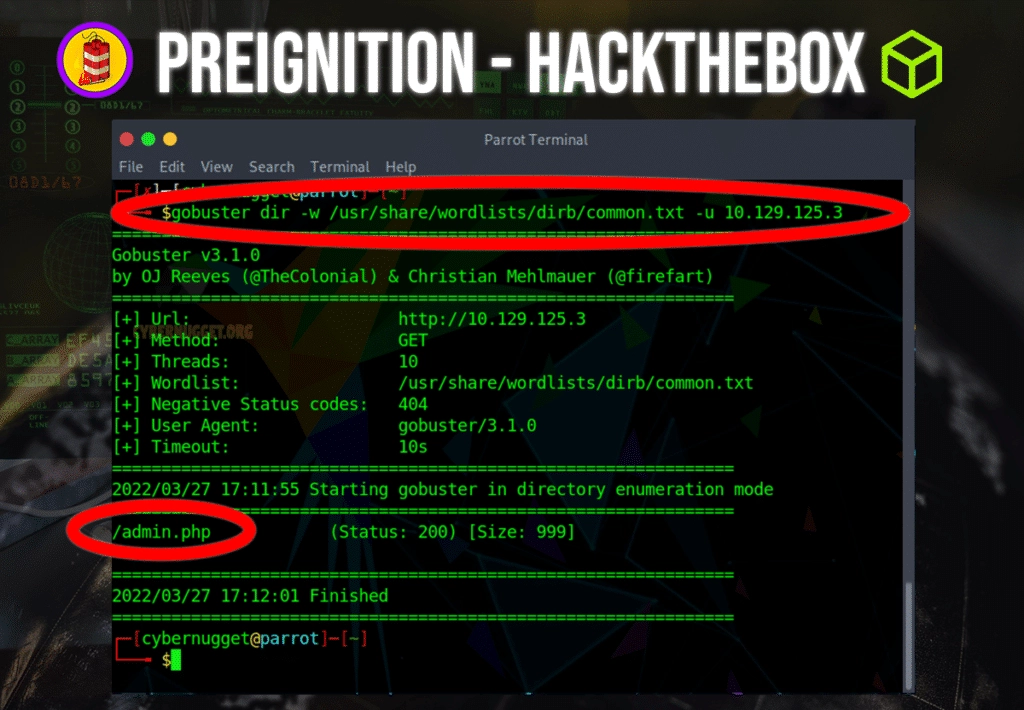
gobuster dir -w /usr/share/wordlists/dirb/common.txt -u 10.129.125.3Task 8
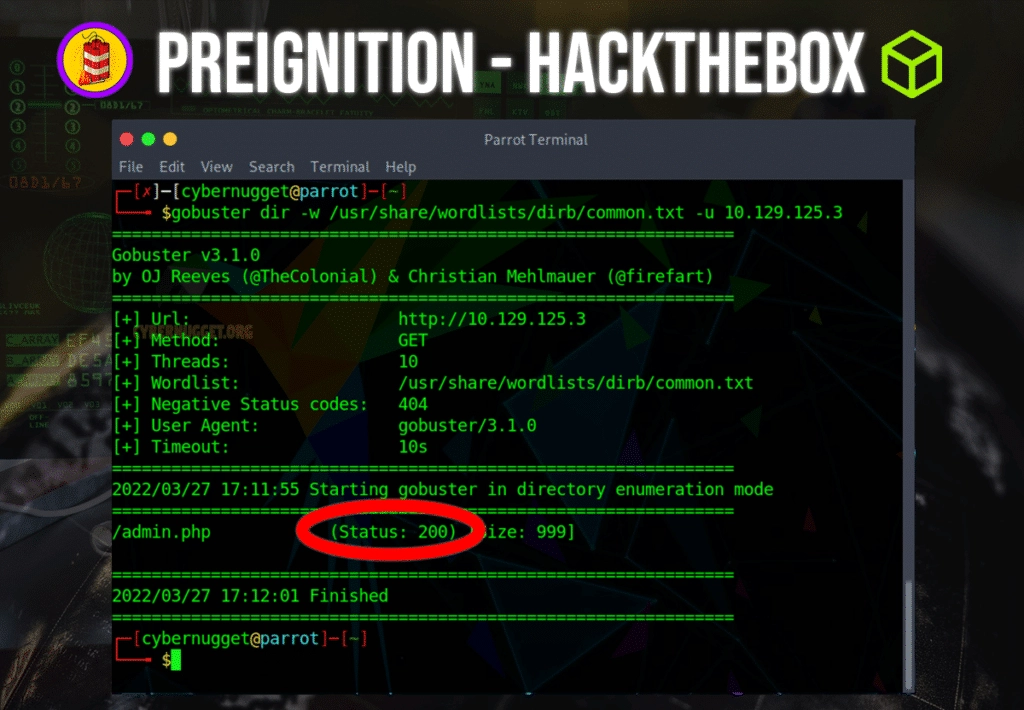
Question: What is the status code reported by gobuster upon finding a successful page?
Answer: 200
Task 9
Submit Flag
Since we can see that there is a directory file named admin.php, we can simply open up a browser and navigate to this directory using the IP address followed by the directory name.

When we navigate to this directory, the first thing that shows up is a login prompt.
CarlosRecruits.com is an independent recruitment website launched in 2023 on a mission to match impactful people with meaningful organizations
Hi! My name is Carlos and I’ve been working in tech for the past 9 years.
I built this website to share my passion for recruitment and tech.
Clicking the heart tells me what you enjoy reading. Social sharing is appreciated (and always noticed).
That’s it. That is my pitch for you to stick around (or browse the site as you please).
If you want to get in contact with me, reach out to me via my socials 🙂

EXPLORE CAREERS
EXPLORE PRODUCTS
“Think of me as the ‘Consumer Reports’ for Impactful Talent.”
Exclusive insights on roles directly in your inbox.


